How do I use MFA to authenticate access to Wasabi using AWS CLI?
It is best practice to protect your account and its resources by using a multi-factor authentication (MFA) device. If you plan to interact with your resources using the AWS CLI when using an MFA device, you must create a temporary session. The steps below outline how to achieve this for any user.
Authenticating Access to Wasabi Using the AWS CLI
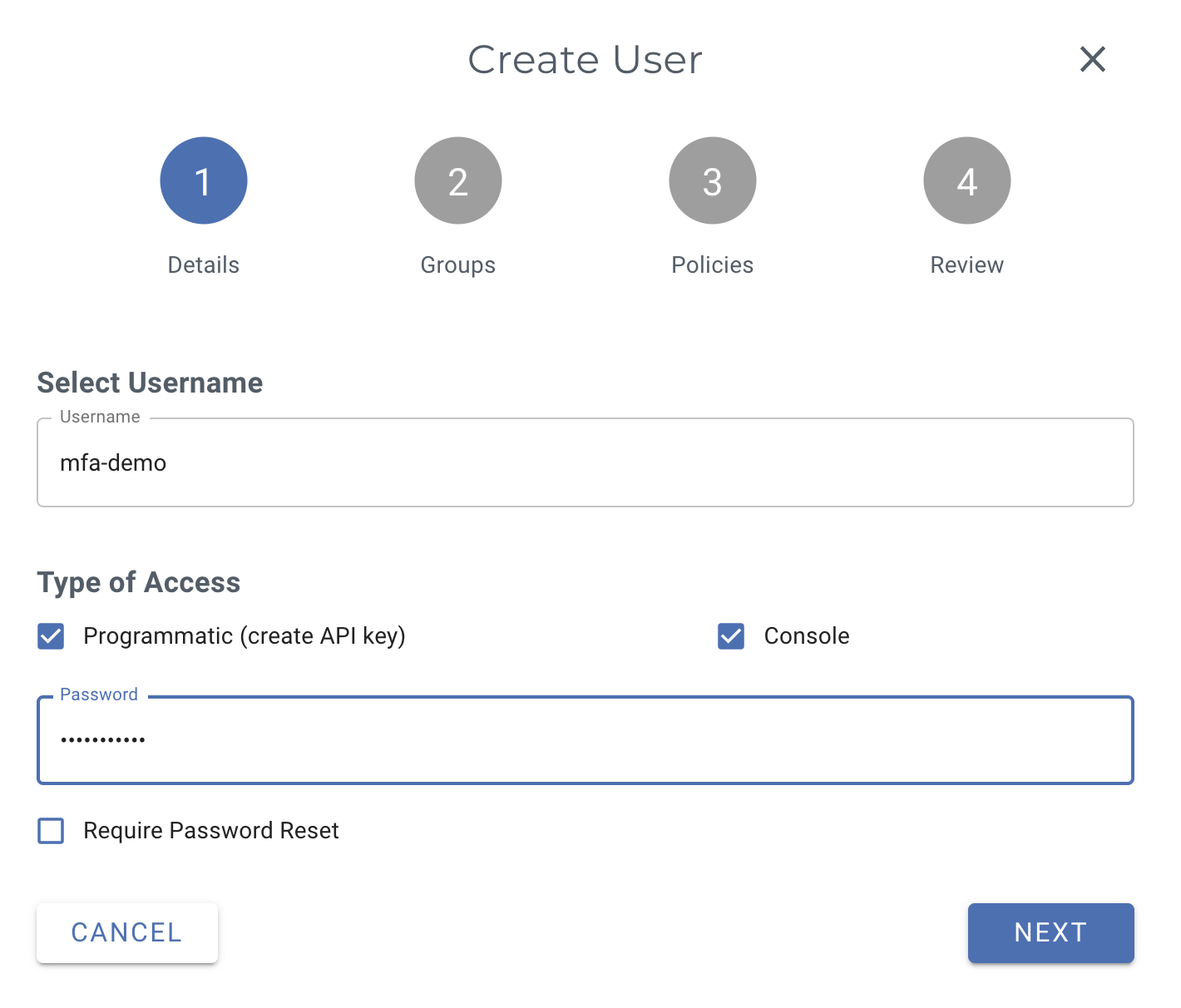
In this example, we create a user called "mfa-demo" and grant them Programmatic and Console access. You can choose whether or not to provide Console access if that is not a requirement. Download the credentials file once the user is created and store it in a secure location, as we will use these credentials later to configure the AWS CLI.
Log in to the Wasabi Management Console https://console.wasabisys.com/login and create a user.
Create an IAM policy that will force the user to authenticate with MFA for any action.
On the Wasabi menu, click Policies. Create a policy based on the user’s requirements. In this example, we are creating a policy called "policy-for-demo-user".
.png)
Actual Policy:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "s3:ListAllMyBuckets", "Resource": "arn:aws:s3:::*" }, { "Effect": "Allow", "Action": "s3:*", "Resource": "*" }, { "Effect": "Deny", "Action": "s3:*", "Resource": "*", "Condition": { "Bool": { "aws:MultiFactorAuthPresent": "false" } } } ] }NOTE: This policy only allows actions on all resources if they are authorized through an MFA authentication both programmatically and through the console.
Once the user and policy are created, navigate to that user and attach the newly created policy to them.
.png)
If not already installed on your system, install the latest version of the AWS CLI.
Use the credential file that you downloaded while creating a user in Step 1. Execute the command below to configure an MFA user's profile. Be sure to use your own Access Key ID and Secret Key ID.
$ aws configure --profile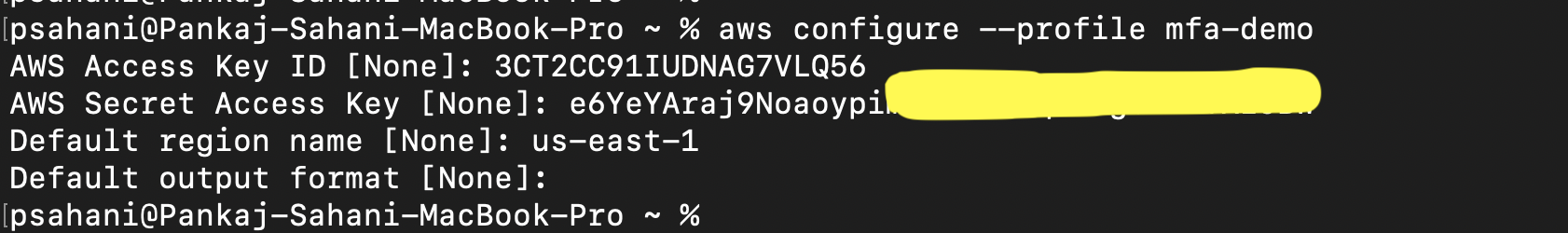
In the Console, navigate to your MFA-created user and activate virtual MFA using any of these tested applications.
.png)
Once the MFA is activated for your user, copy the ARN of this user and store it in a secure location.
.png)
On the CLI, run the sts get-session-token command. Replace the variables with information from your account, resources, and MFA device.
$ aws sts get-session-token --serial-number --token-code --profile --endpoint-url=https://sts.wasabisys.comYou will receive an output with temporary credentials and an expiration time (default: 12 hours), similar to the following.
{ "Credentials": { "SecretAccessKey": "secret-access-key", "SessionToken": "temporary-session-token", "Expiration": "expiration-date-time", "AccessKeyId": "access-key-id" } }.png)
You can specify an expiration duration (in seconds) using the --duration-seconds option in the sts get-session-token command, where the value can range from 900 seconds (15 minutes) to 129600 seconds (36 hours). If you are using root user credentials, the range is from 900 seconds (15 minutes) to 3600 seconds (1 hour).
Edit the credentials file in the .aws folder in the user’s home directory to add a new profile configuration for issuing MFA-authenticated commands. Below is an example profile configuration.
In this example, we are configuring a profile name as "mfa-demo-temporary".
[mfa-demo-temporary] aws_access_key_id = example-access-key-as-in-returned-output aws_secret_access_key = example-secret-access-key-as-in-returned-output aws_session_token = example-session-Token-as-in-returned-output.png)
After the credentials expire, execute the get-session-token command again and export the returned values either to the environment variables or to the profile configuration.
NOTE: Consider running a script or a cron job in the background that checks for “expiration” from the output of the get-session-token command, then prompting for a re-authentication.
To show the working of this authentication, we have uploaded an object to a Wasabi bucket with regular credentials and temporary sts credentials. Even though this user has complete permission to perform any S3 action, it will get denied due to the forced MFA policy. The operation is only successful when the temporary sts credentials are used, which is governed by MFA.
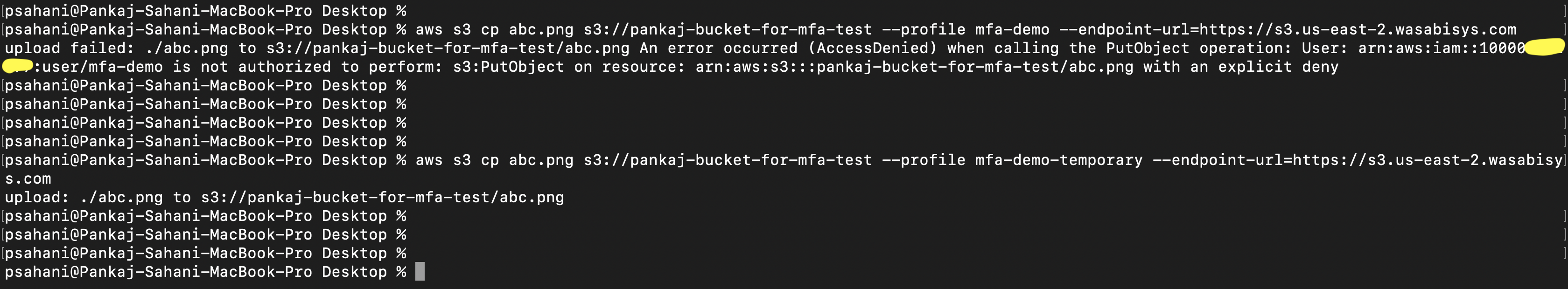
NOTE: This code example discusses the use of Wasabi's us-east-2 storage region. To use other Wasabi storage regions, use the appropriate Wasabi service URL as described in Service URLs for Wasabi's Storage Regions.
Appendix
If you do not wish to use named profiles as demonstrated above, you may also use temporary credentials with environment variables.
To use temporary credentials, export their values to environment variables using the following commands.
Linux:
export AWS_ACCESS_KEY_ID=example-access-key-as-in-previous-output export AWS_SECRET_ACCESS_KEY=example-secret-access-key-as-in-previous-output export AWS_SESSION_TOKEN=example-session-token-as-in-previous-outputWindows:
set AWS_ACCESS_KEY_ID=example-access-key-as-in-previous-output set AWS_SECRET_ACCESS_KEY=example-secret-access-key-as-in-previous-output set AWS_SESSION_TOKEN=example-session-Token-as-in-previous-outputIf you set the environment variables, be sure to unset them before making the get-session-token call again using these commands.
unset AWS_ACCESS_KEY_ID unset AWS_SECRET_ACCESS_KEY unset AWS_SESSION_TOKENIf you prefer this approach, then you will not need to specify "--profile" argument in your commands.