How do I use Opti9 Observr with Wasabi?
Wasabi has been validated with Opti9's Observr. Observr utilizes artificial intelligence and machine learning to baseline, monitor, and identify suspicious activity within the backup infrastructure, allowing it to predict and help prevent a ransomware attack before it starts.
1. Introduction
The Wasabi and Observr joint solution couples Veeam’s best-of-breed backup and replication software, Wasabi’s secure cloud storage service, and Opti9’s innovative ransomware detection technology to instantly strengthen customers’ security posture when it comes to their backup strategy. Observr detects anomalous actions at a frequency that may indicate ransomware or other malicious activities are occurring. This includes monitoring changes to job definitions, encryption settings, retention settings, backup and replica sizes, deletion events, disabling jobs, and incremental backup and replica change rates. Observr also provides access to Opti9’s hybrid cloud management platform, OptiXdashboard, along with a 24x7, 15-minute SLA, and a suite of Veeam-specific reports and tools.
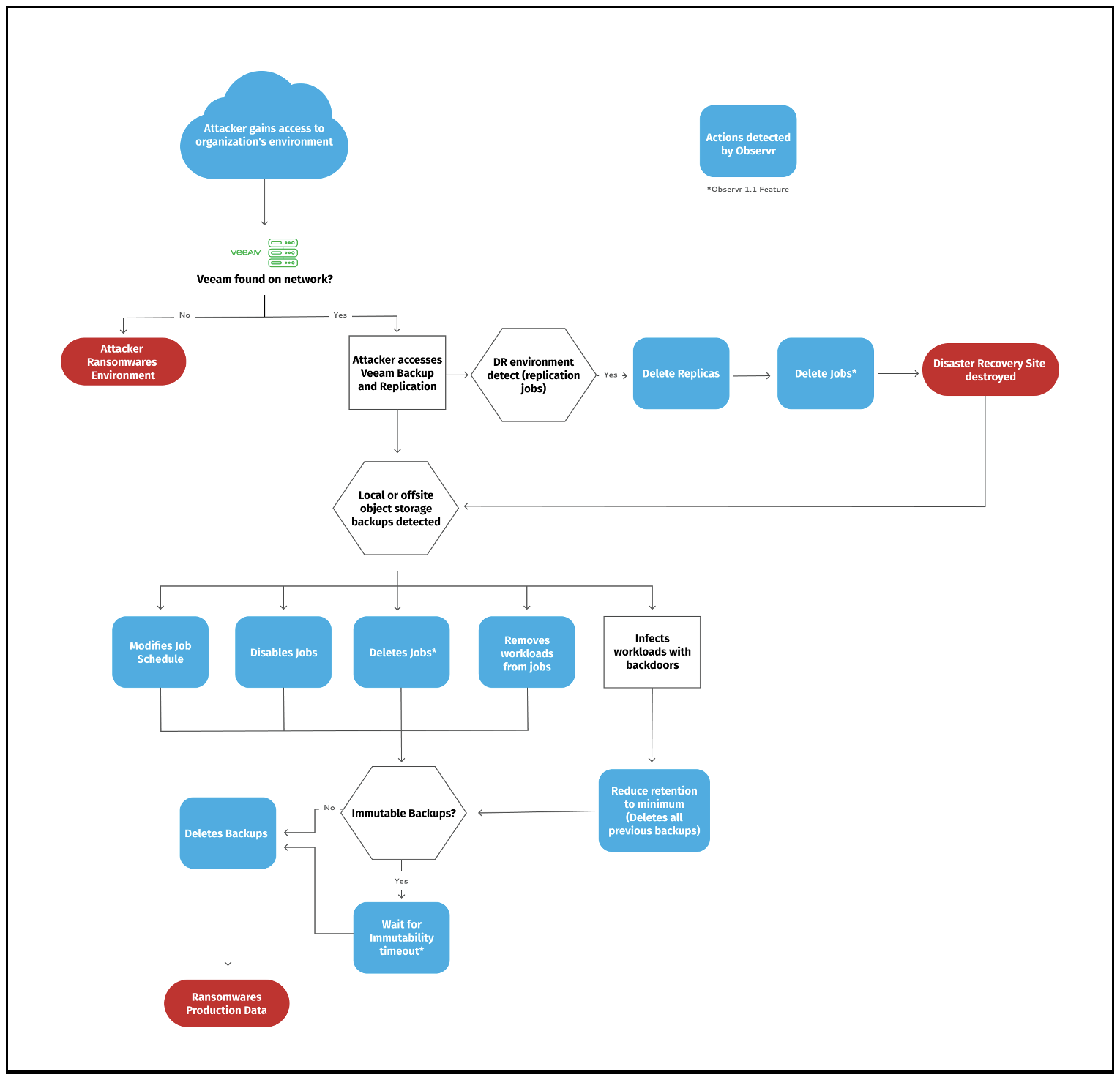
The workflow below details the anatomy of an attack. It demonstrates how attackers compromise Veeam and where/how Observr helps.
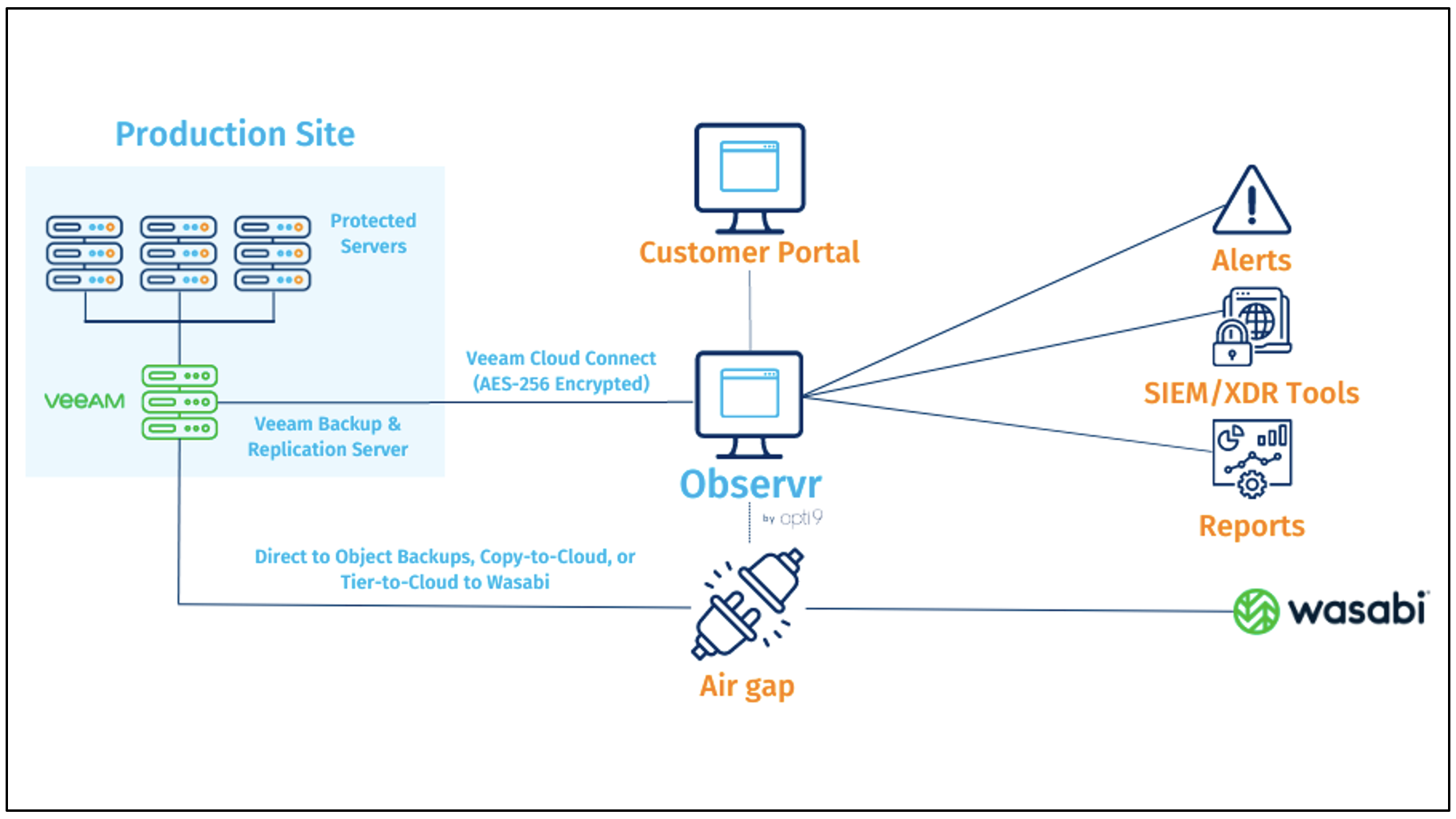
2. Reference Architecture
3. Prerequisites
The customer must be using licensed Veeam software - v10a or higher. Customers can utilize Wasabi in any capacity – direct to cloud, copy to cloud, or tier to cloud.
Attach Observr to Veeam as a “service provider” with managed bit enabled
An active Wasabi account
Note: Automated air-gap with Wasabi will only work via the use of a customer-deployed script, which is provided upon request.
4. Configuration
Observr is completely agentless, which means the solution can be up and running within minutes. It utilizes Veeam’s proprietary and encrypted CloudConnect protocol to send data between the Veeam Backup & Replication server and Opti9’s SaaS platform. Once connected, Observr utilizes Veeam’s console API to pull metrics and metadata from the Veeam install. Observr then monitors the Veeam configuration, backup sizes, incremental change rates, and RPOs. Its machine learning jobs will detect suspicious activity based on that specific site’s activity history. Besides running Veeam, the only other requirement to using Observr is an internet connection.
During the onboarding process, Opti9 will generate authentication credentials for the organization’s Veeam instance. The organization will add Observr as a CloudConnect service provider within Veeam and grant Observr remote permissions to connect to the Veeam API. From there, the organization will be able to use Observr's web interface to configure threat monitoring, alerting, and other actions.
Organizations that already backup their data to Wasabi don’t need to make any changes to utilize Observr. However, if they would like to configure Observr to automatically air-gap their Wasabi data, an additional script is required. Alternatively, customers can choose to have their offsite backups first land on Opti9’s backup storage before being shipped to Wasabi. This allows for the automated air-gap out of the box, the addition of a backups recycle-bin, and the ability to use cloud-based synthetic creation (CloudConnect features)
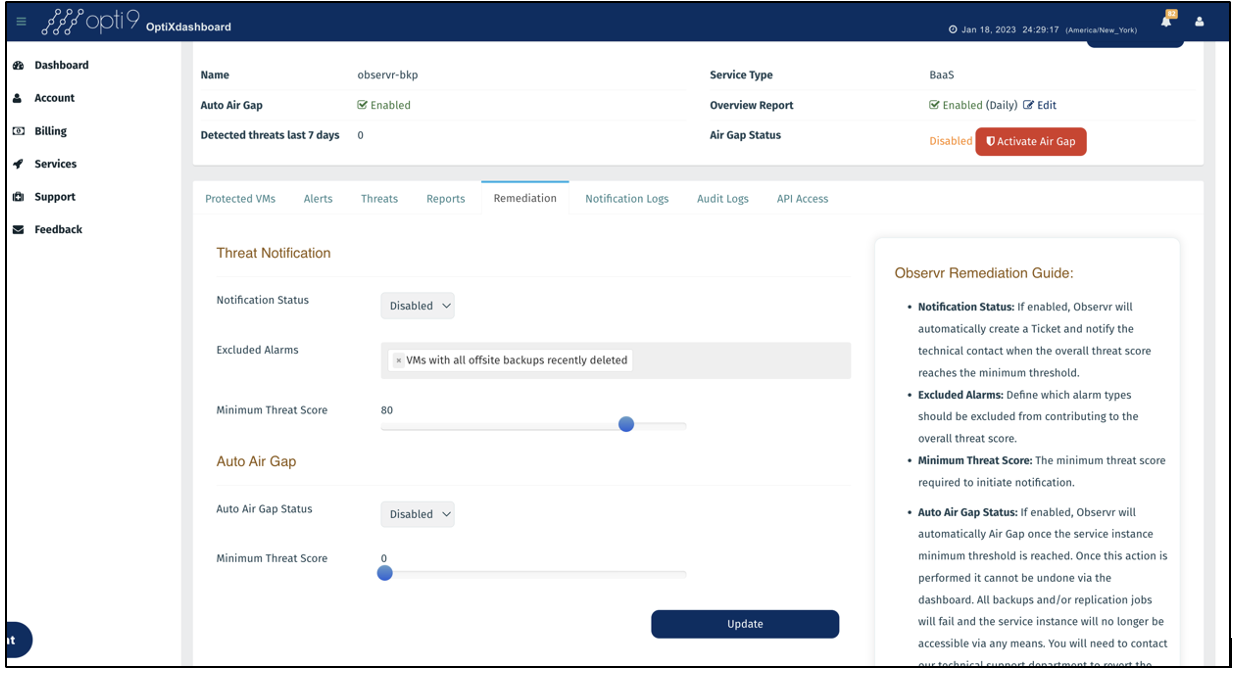
Observr features completely external and customizable RPO monitoring, retention policy violation reporting, Veeam alarm routing, compliance reporting, real-time and per-workload protection details useful for forensics.
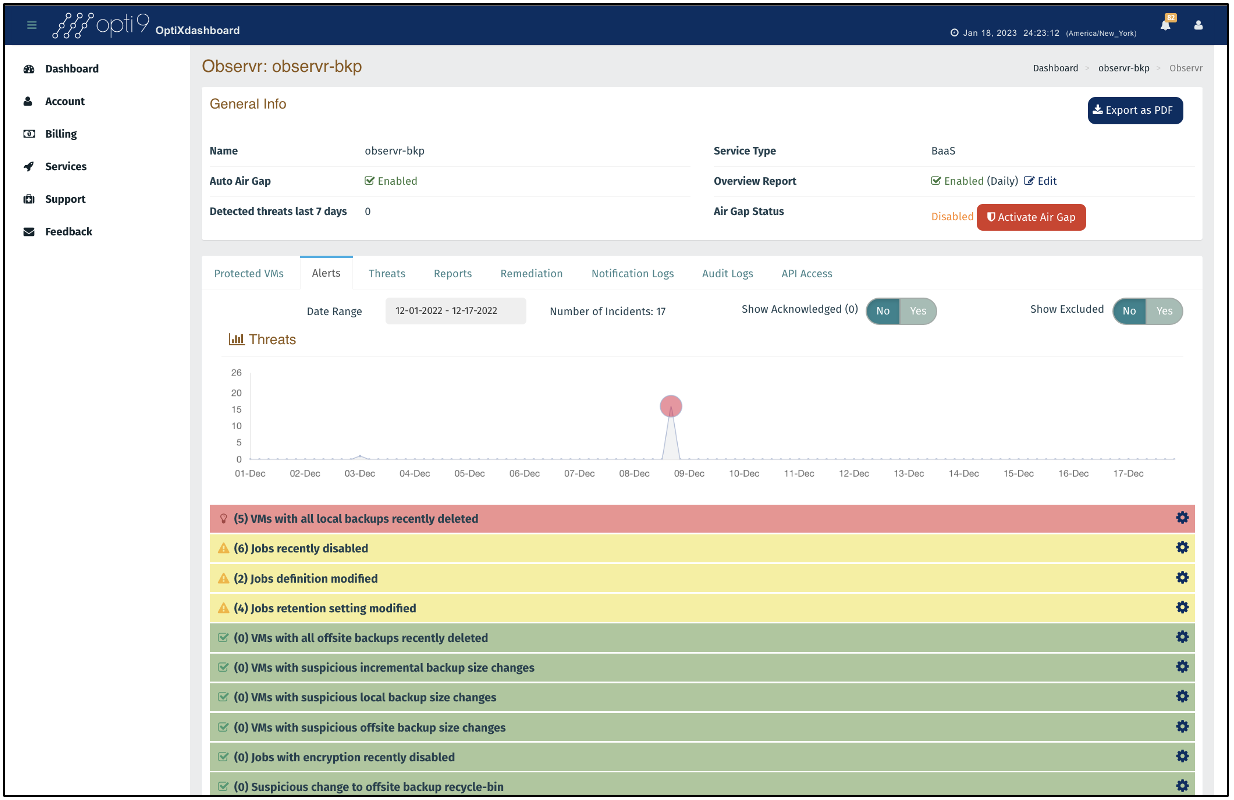
Threat events are created when suspicious activity is detected, with the ability to configure alerts/alarms.
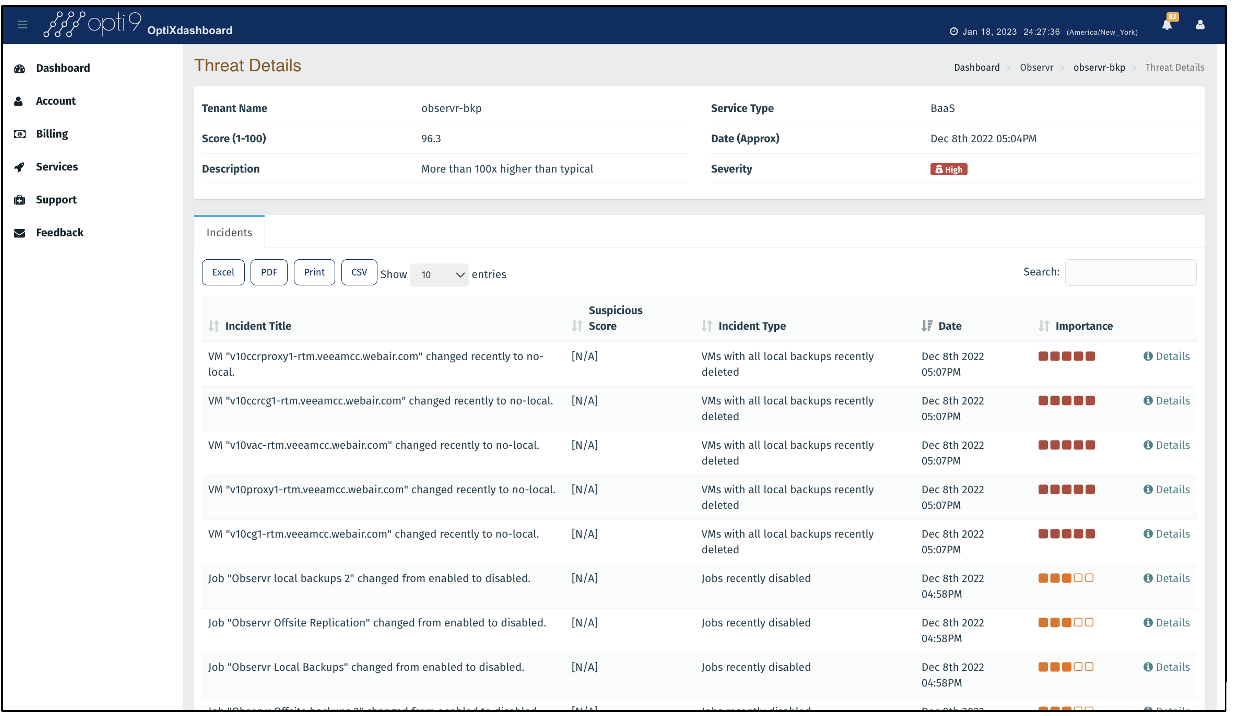
In the event of a threat, Observr provides the ability to configure automated air-gap as remediation.
5. Use Cases
Use case 1: Companies seeking additional layers of protection from threats specifically targeting their backup and replication environments.
Use case 2: Companies who are looking to harden their security stance quickly, and without having to install any additional software.
Use case 3: Companies with mature security requirements, who are looking to monitor the new attack vector created by the backup & DR infrastructure and integrate and correlate the data with their existing security tools.
Use case 4: Companies that are currently using Veeam, or thinking of using it, but are looking for additional ransomware and security protection such as those offered by other vendors.
Use case 5: Companies looking to protect their offsite backup & DR infrastructure from attackers via the use of automated or manual air-gap capabilities.
Use case 6: Companies that utilize security tools such as SIEM, SOAR, MDR, XDR, or who contract with an MSSP and would like to integrate those platforms into the Veeam-specific threat detection and alerting provided by Observr.