How do I use Peer Global File service to Backup to Wasabi?
Wasabi has been validated to work with Peer Global File service (PeerGFS). Cloud Backup and Replication brings file to object replication into Peer Software’s capabilities for enterprise NAS environments. Leveraging the same real-time engine that powers Peer Software’s multi-site, multi-vendor replication, Cloud Backup and Replication efficiently pushes data into Wasabi hot cloud storage in an open format that is immediately consumable by other applications and services.
To learn more about our solution, please refer to our joint solution brief.
Note: The data restoration process is handled by your specific backup software application. As there are many potential variables that will affect your unique environment, it is strongly recommended that you seek the guidance of your backup software's technical support team in the event that you encounter difficulty, or have application-specific inquiries.
1. Prerequisites
Peer Global File Service v5.1.0.20230105 and newer.
License for Peer Global File Service v5.1 or newer required.
Contact your Peer Software Support representative to enable the S3 Compatible destination.
Microsoft SQL Server or SQL Server Express database.
An active Wasabi cloud storage account.
2. Architecture Diagram
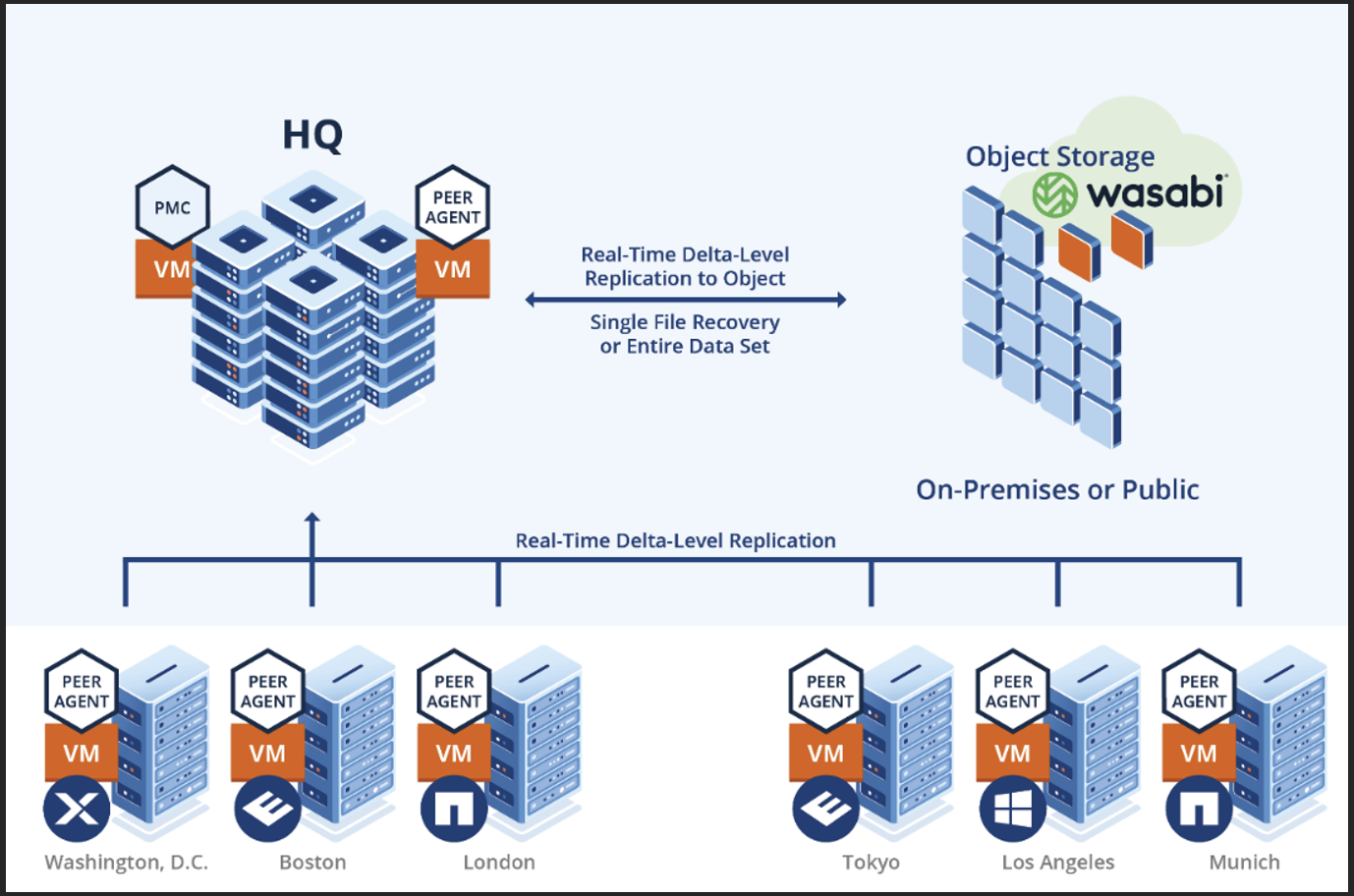
3. Creating a Cloud Backup and Replication Job
3.1 Open the Peer Management Center. From the File menu, select "New Job" (or click the New Job button on the toolbar). The "Create New Job" wizard displays a list of job types you can create. Select "Cloud Backup and Replication" and click on "Create".
3.2 Enter a name for the job in the dialog that appears and click "OK".
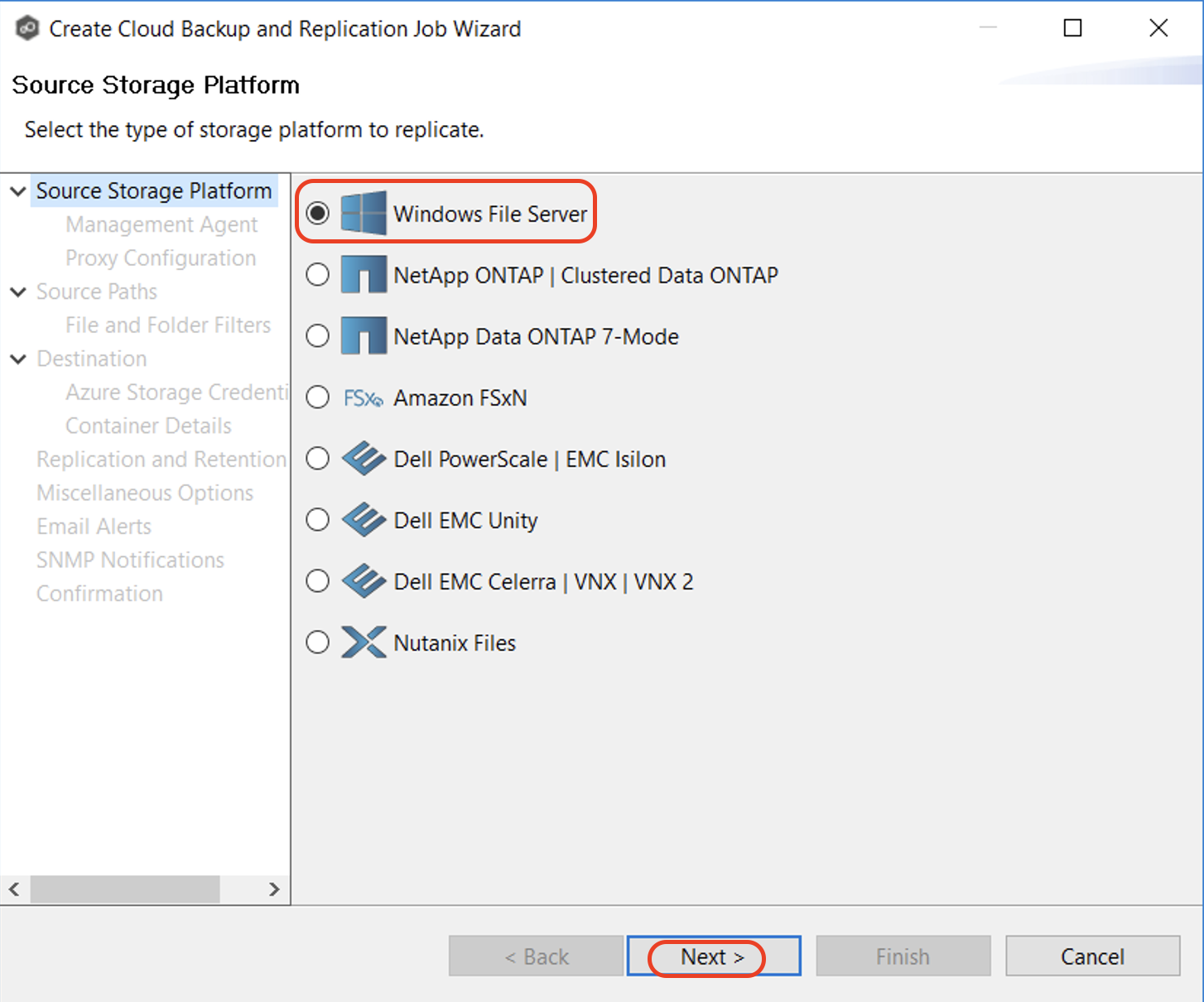
3.3 On the "Source Storage Platform" page, select the type of storage platform you want to replicate. Click "Next" to continue. This page lists the types of source storage platforms that Cloud Backup and Replication supports. The source storage device hosts the data you want to replicate.
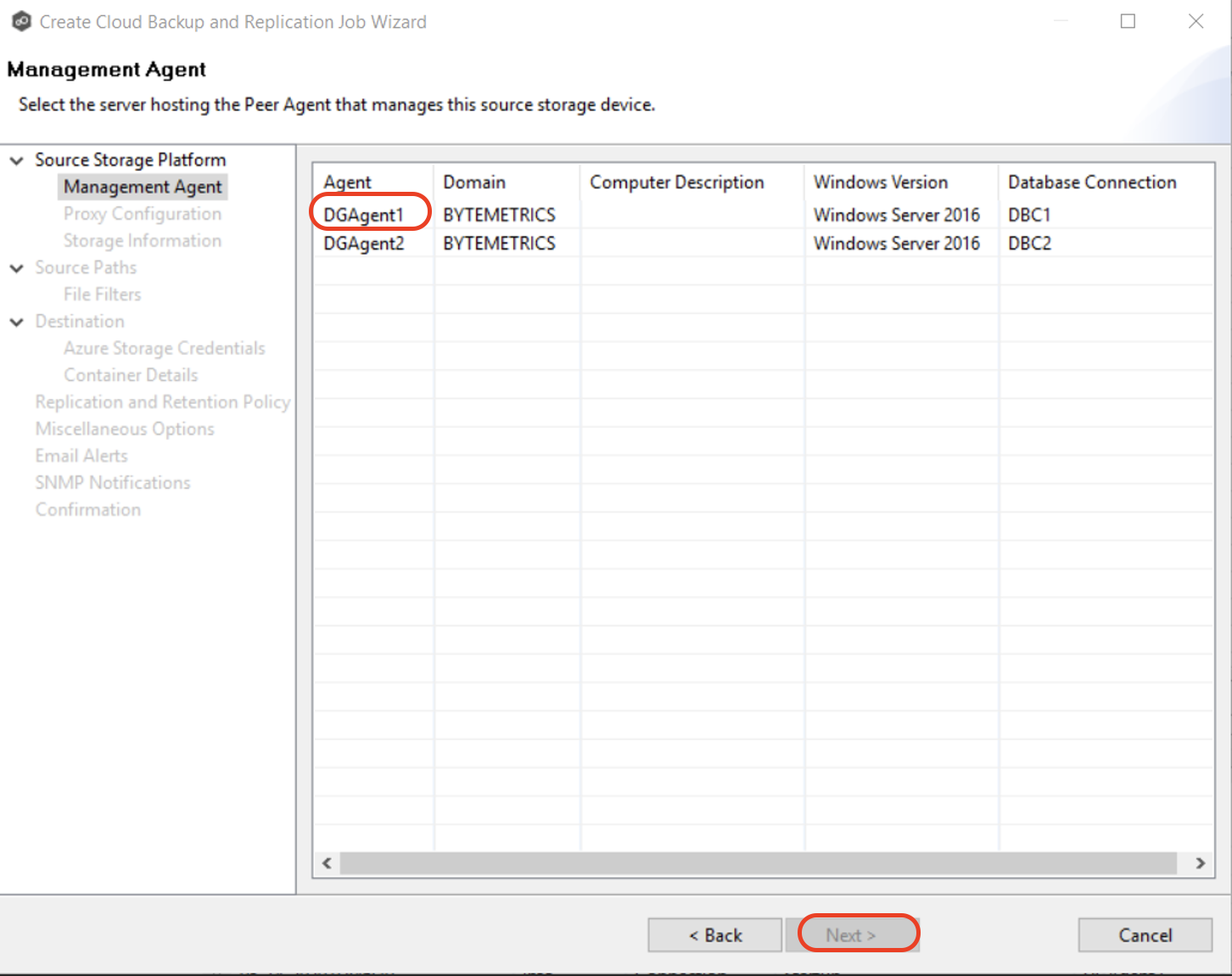
3.4 Select the Management Agent for the volume/share/folder you want replicated. Each storage device that you want to replicate must have a Peer Agent that manages that device. The Peer Agent that manages a device is known as its Management Agent.
Note: If you select an Agent that does not have a database connection listed in the Database Connection column, a message prompts you to create the connection:
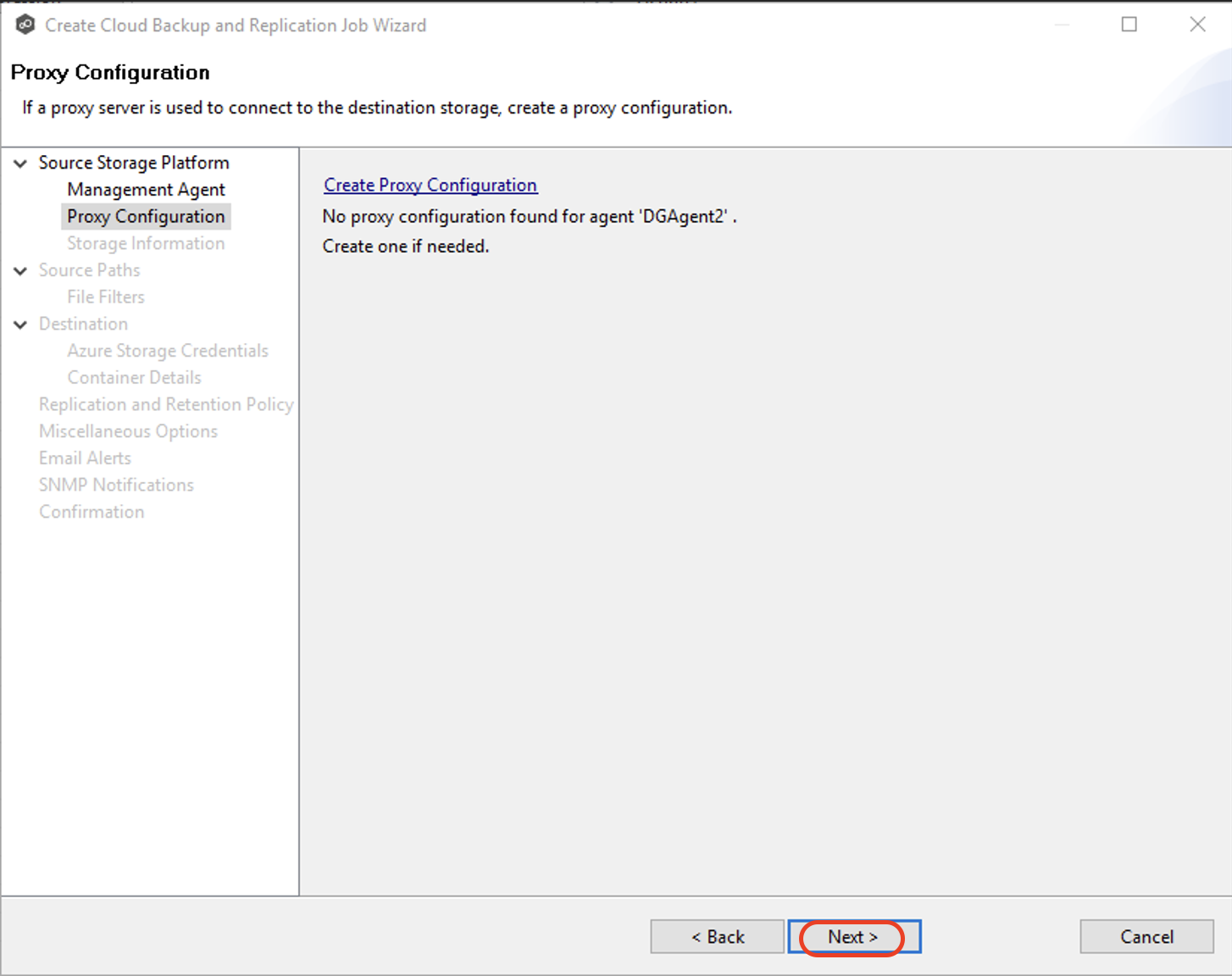
3.5 Proxy Configuration. If you do not need a proxy server to connect to outside networks, click "Next".
If you do need a proxy server to connect to outside networks, you have three options:
Create a new proxy configuration.
Use the existing proxy configuration. If there is an existing proxy configuration, details about the configuration will be displayed on the page. You may have created one in advance through Cloud Back and Replication Preferences or when you created another Cloud Backup and Replication job. Once a proxy configuration is created for a source storage platform, that proxy configuration is used for all Cloud Backup and Replication jobs using that agent.
Edit an existing proxy configuration. Click on "Edit Proxy Configuration" to edit the existing proxy.
Please review Proxy Configuration for more details.
Note: If you edit the proxy configuration, it affects other jobs using the same agent. Editing an existing proxy configuration has the potential to create problems with the other jobs.
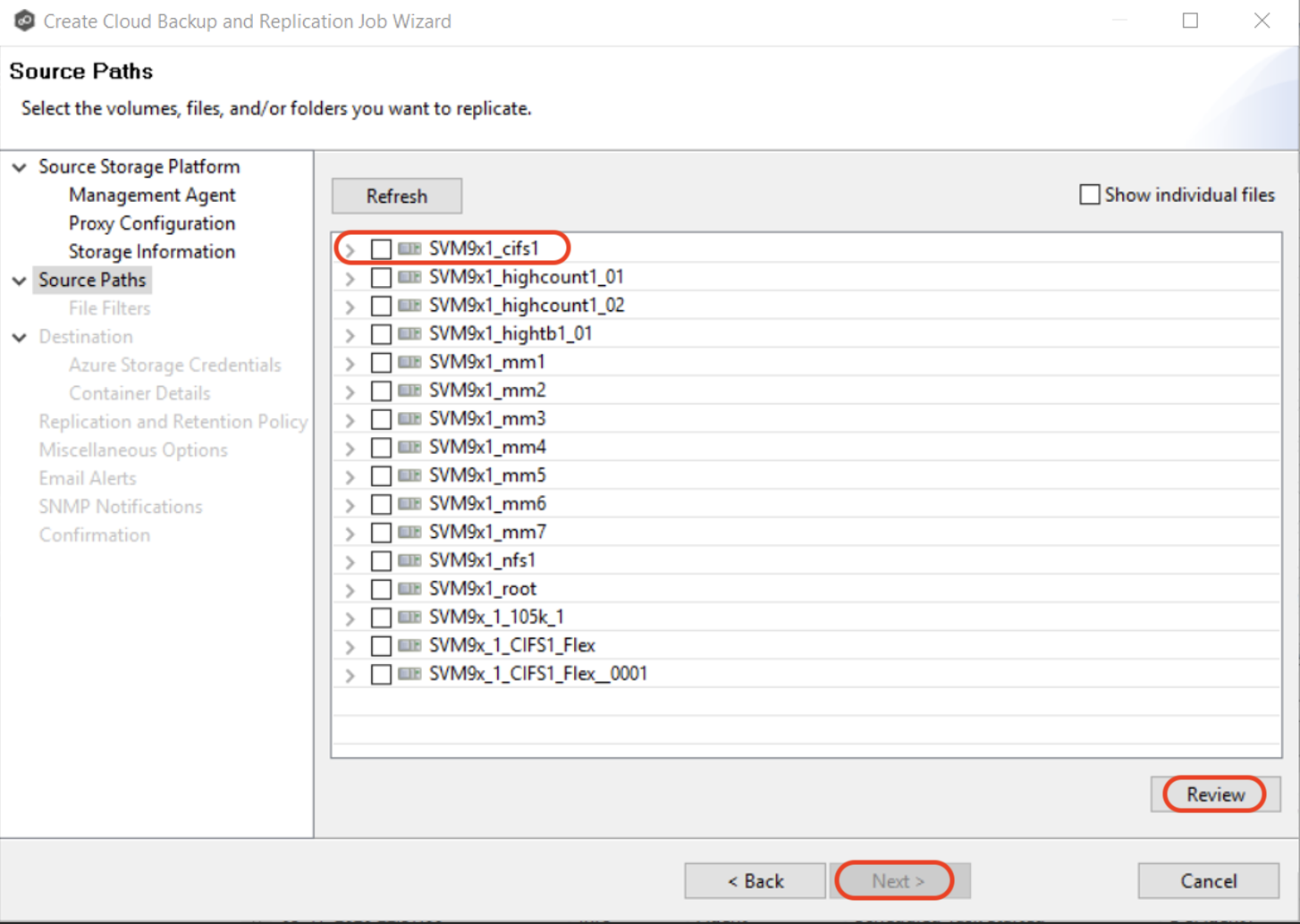
3.6 Select the paths to the files/folders/volumes you want to replicate. Click "Review" button to review your selections and then click "Next".
The Source Paths page displays a list of available volumes to replicate. You can choose to replicate an entire volume or selectively replicate files and folders. The files/folders/volumes selected for replication are referred to as the watch set.
Select the volume checkbox to replicate the entire volume (all files and folders, including subfolders and their files).
Expand the volume, scroll to the bottom of the expanded list, and select All Files to replicate all files at the root level of the volume (but no folders).
Expand the volume, find the desired folder, and select its checkbox to replicate a specific folder and its content (including subfolders and their files).
Expand the folder and select All Files to replicate all files within a specific folder (but not the folder).
To replicate specific files and folders, select the "Show individual files" checkbox, expand the folders, and select the files and folders you want to replicate.
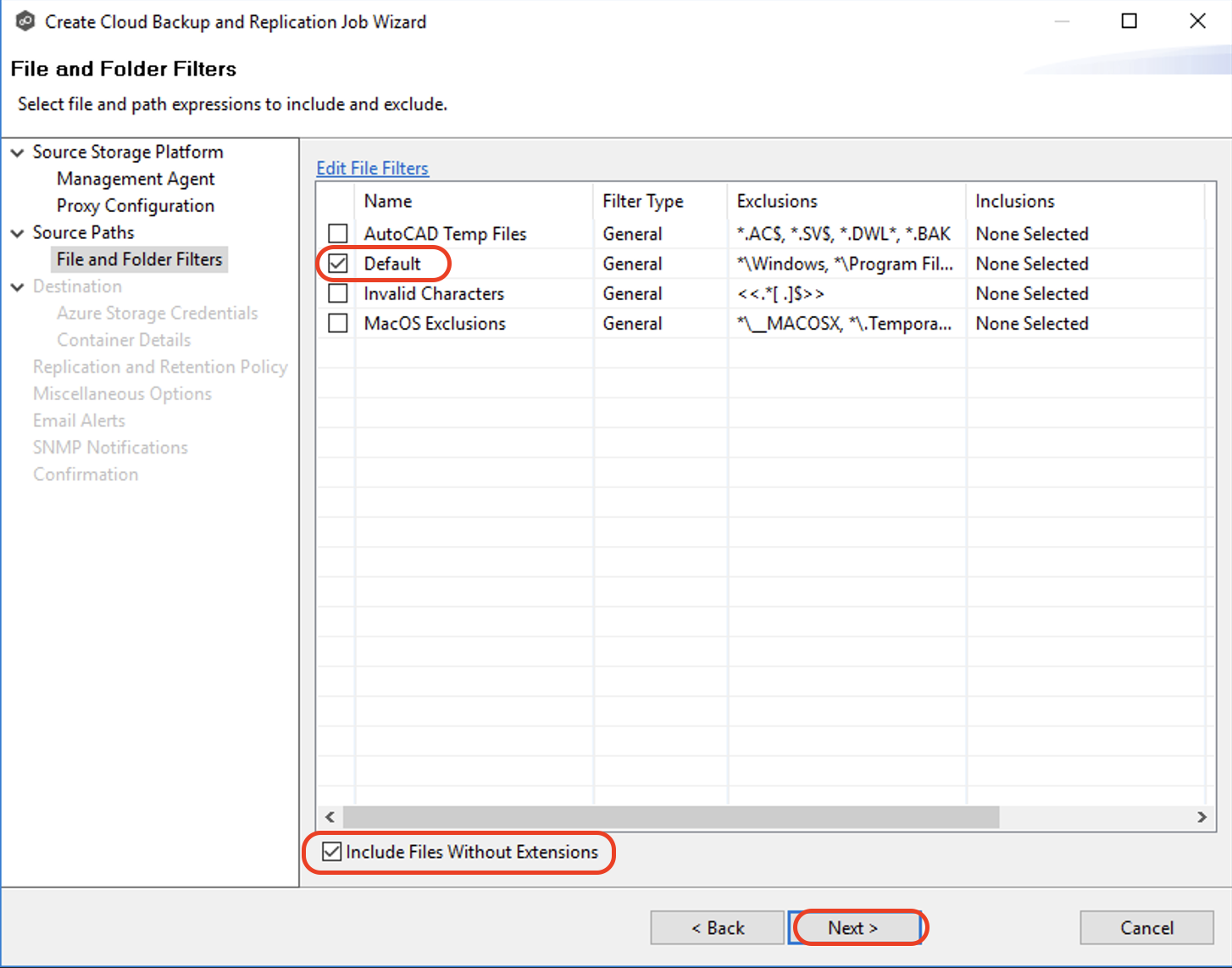
3.7 Select the file and folder filters you want to apply to the job. Select the Include Files Without Extensions checkbox if you want to replicate files that do not have extensions. Click "Next" to continue.
The File and Folder Filters page displays a list of file and folder filters. By default, all files and folders selected in the Source Paths page will be replicated. A file or folder filter enables you to exclude and/or include files and folders from the job based on file type, extension, name, or directory path. Any file or folder that matches the filter is excluded or included from replication, depending on the filter’s definition.
Note: Files without extensions are ignored during replication unless you select this checkbox.
3.8 On the Destination page, select the S3 Compatible destination. Click "Next" to continue.
Note: Contact your Peer Software Support representative to enable the S3 Compatible destination.
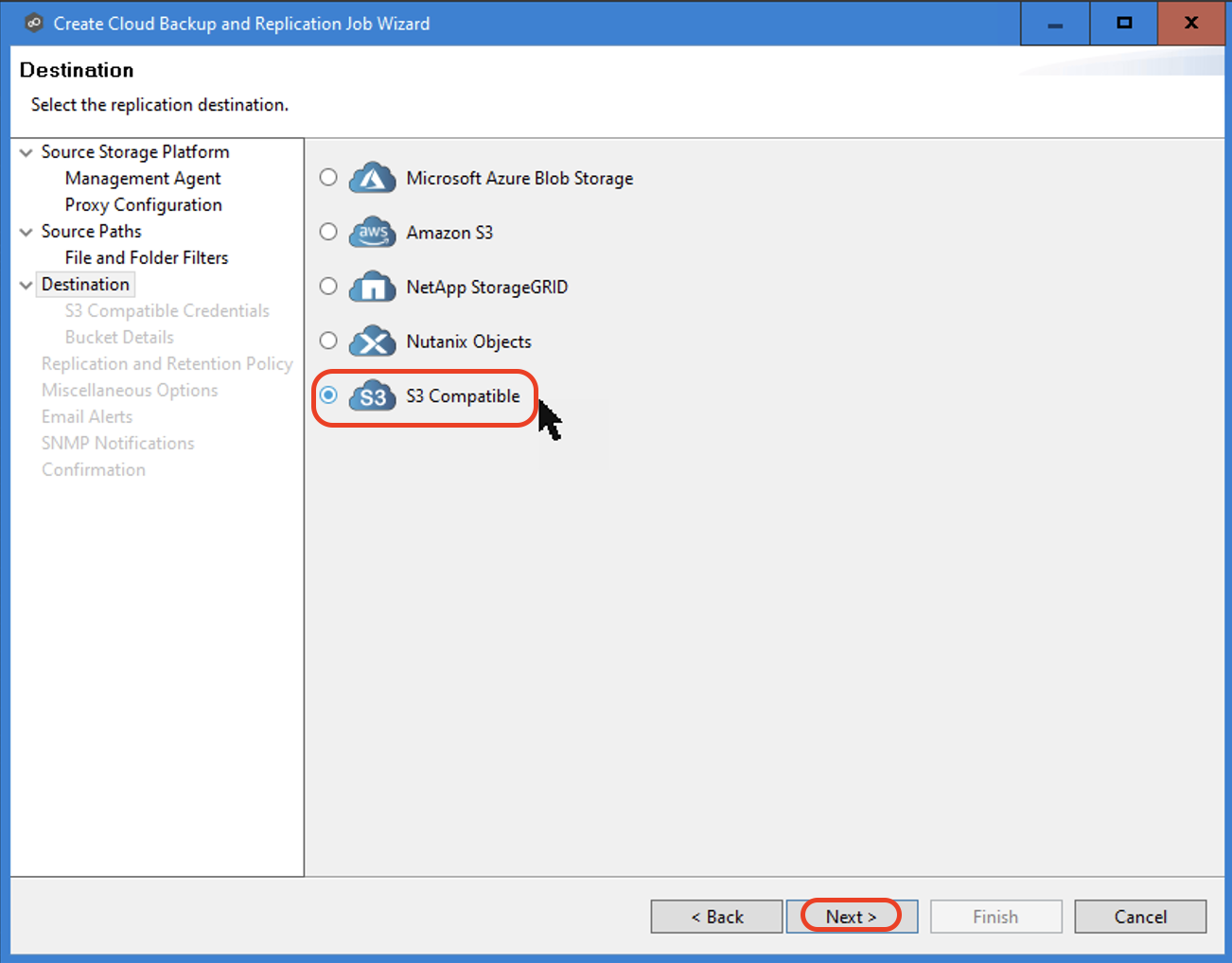
3.9 Input the following crendentials-
Description- "Wasabi" or any name you'd like to apply.
Access- Access key for the Wasabi bucket. Refer to creating a sub-user and access and secret keys.
Secret keys- Secret key for the Wasabi bucket. Refer to creating a sub-user and access and secret keys.
Service Point- Enter the appropriate Wasabi service url (should end in .wasabisys.com). Please use the appropriate Wasabi service URL as described in our Wasabi Service URLs article.
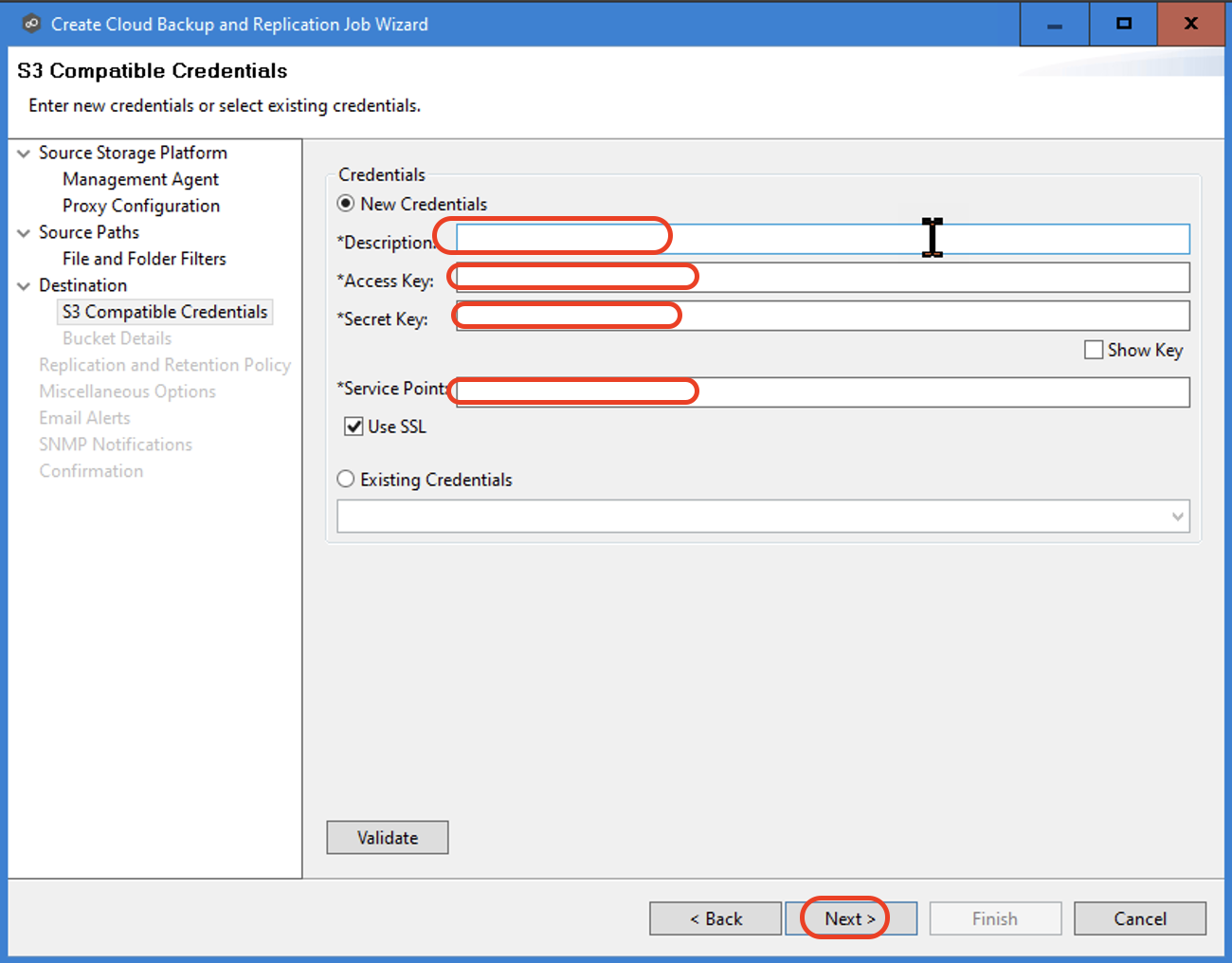
3.10 Create a new Wasabi bucket or choose an existing one from the drop down list. Click "Next" to continue.
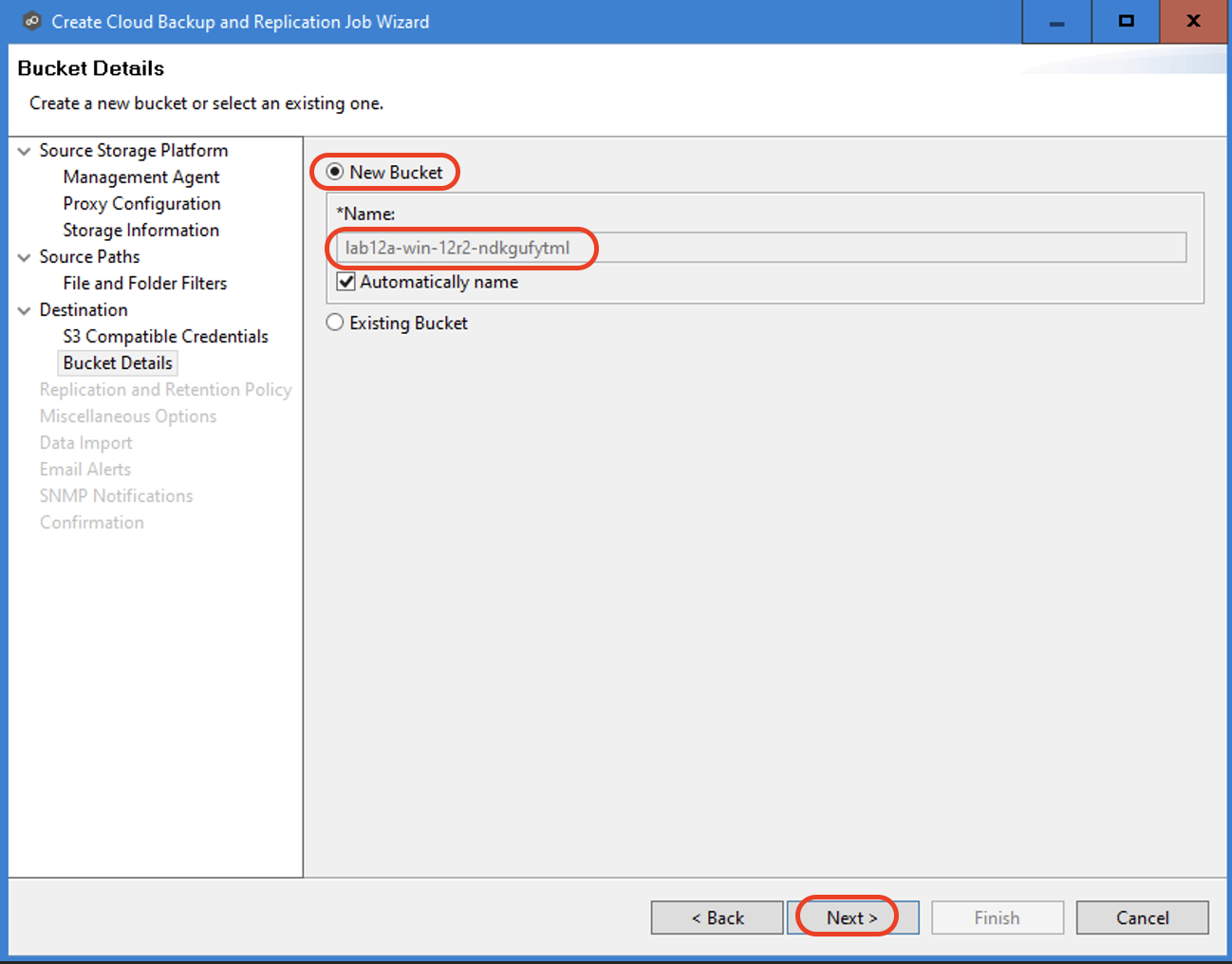
3.11 On the Replication and Retention Policy page, select New Policy or Existing Policy from the dropdown list. If you select a new policy, input a "Name" for the new policy.
Select "Enable Backup with Destination Snapshots" if you want to replicate what is on premises to the destination storage device, while taking destination snapshots at specified points in times. Then click "Next" to continue.
Each Cloud Backup and Replication job must have a Replication and Retention policy. A Replication and Retention policy specifies:
How often you want to scan the storage device for replication or if you want to replicate in real-time.
Whether you want to take snapshots of the data. A snapshot captures the state of a file system at a point in time. There are two types of snapshots:
A destination snapshot captures an image of the data on the destination storage device immediately after replication. Destination snapshots are useful for recovering data from different period of times. Destination snapshots track versions of changed files and file system structure that can be used for data recovery. For more information about recovering data, see Recovering Data.
A source snapshot captures an image of the data on the source storage device immediately before replication. Sources snapshots are useful for replicating open and locked files, which otherwise may not be able to be replicated. A source snapshot also ensures that the replicated data is coming from a static version of the source file system. For details about using source snapshots, see step 3.14.
How long you want to retain destination snapshots.
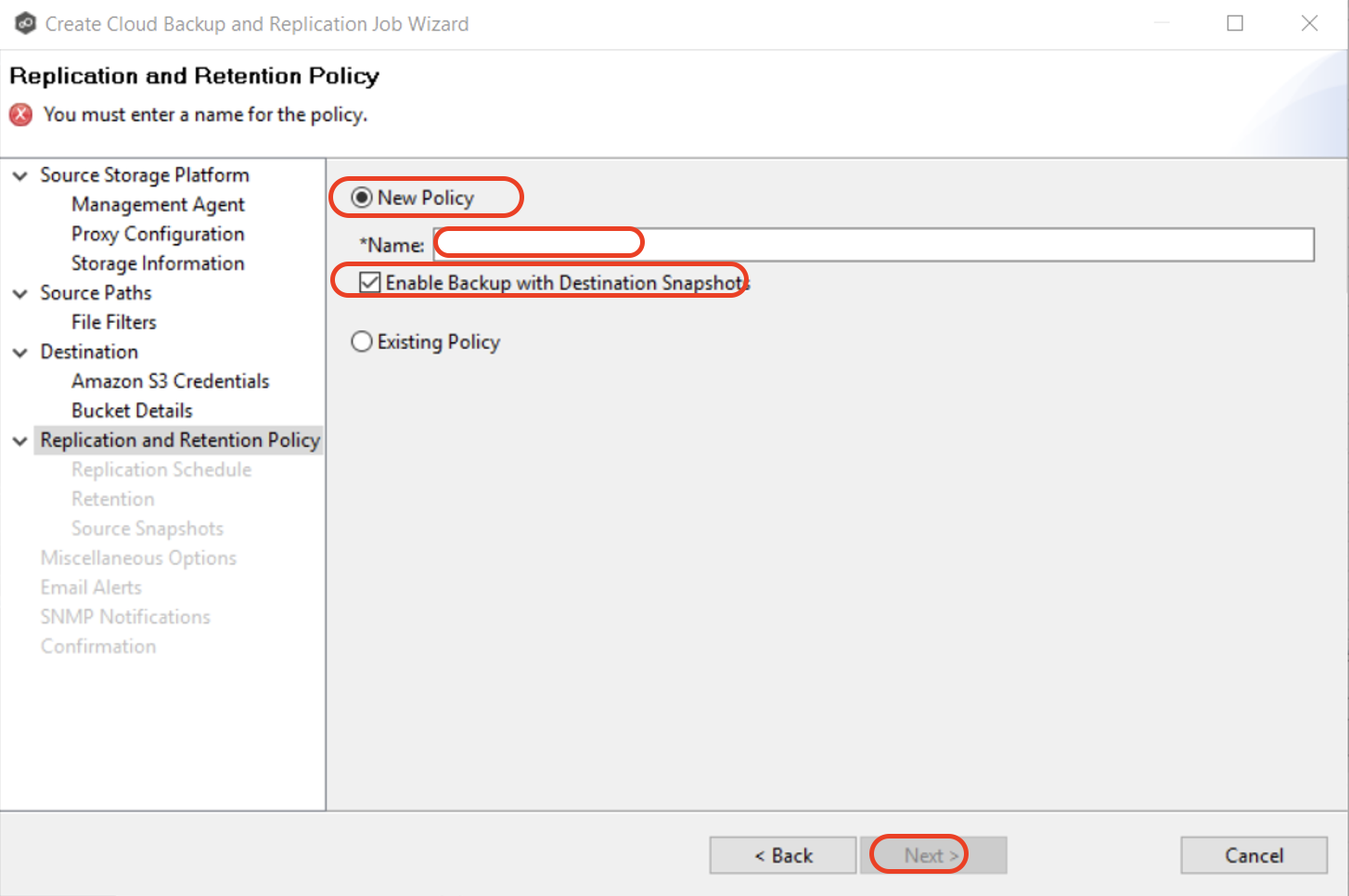
3.12 On the Replication Schedule page, select the frequency of the replication. Click "Next" to continue. The Replication Schedule page enables you to select the frequency of the replication and when snapshots should be taken.
Scheduled Scans- Select this option if you want to replicate files on a scheduled basis. A scan of changes to the file system occurs on a scheduled basis, either daily or weekly, and replication of changes occurs as the scan progresses.
Batched Real-time -Select this option if you want to continuously monitor changes to the file system but replicate changes on scheduled basis. Changes are monitored in real-time and only the latest version of changed file is replicated at scheduled times. An initial scan can be performed to establish a baseline.
Continuous Data Protection- Select this option if you want continuously monitor changes and replicate changes in real-time. Whenever a file changes, the change is replicated in real-time.
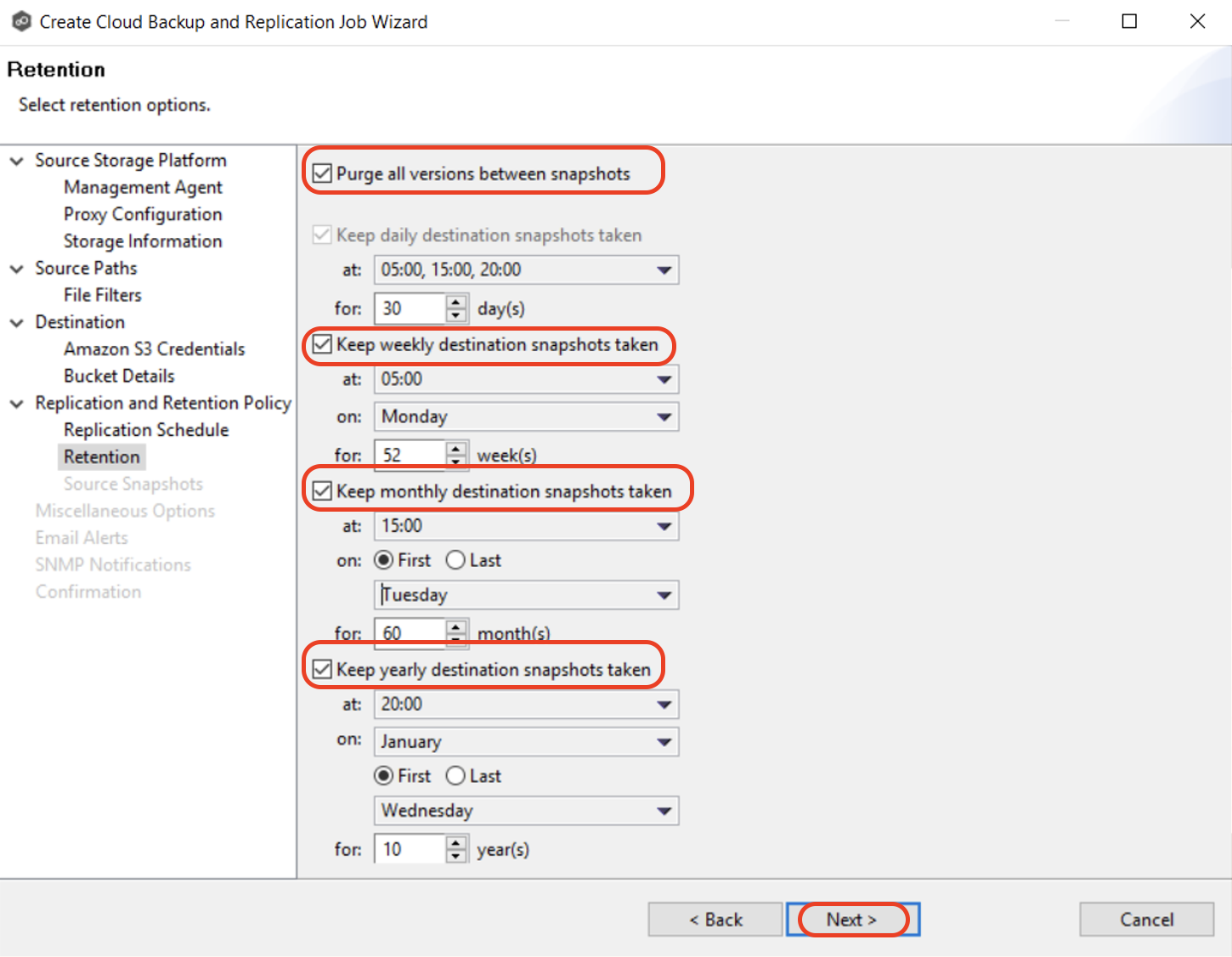
3.13 Select the retention options. Then click "Next". The Retention page enables you to define how long you want to retain destination snapshots. You have the option to retain destination snapshots on a daily, weekly, monthly, and yearly basis.
Note: The options vary according to the replication schedule you selected. If you did not select the Enable Backup with Destination Snapshots in Step 3.11, the Retention page will not appear.
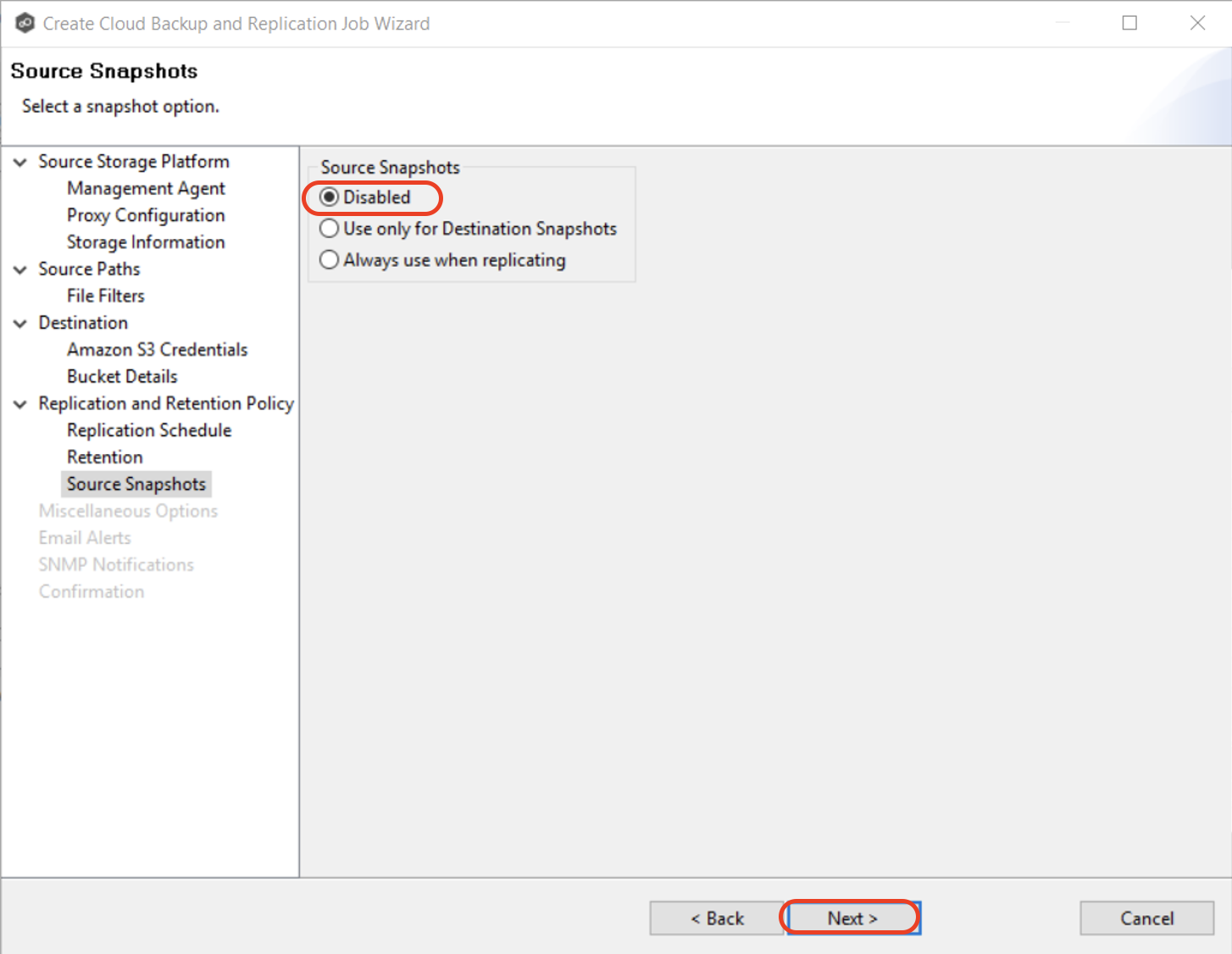
3.14 Select a source snapshot option and click "Next" to continue.
A source snapshot is a read-only point-in-time version of the volume.
Select the Disabled option if you do not want to take source snapshots.
Select the Use only for Destination Snapshots option when you want the source snapshot to be stored on the destination storage as the destination snapshot rather than an actual destination snapshot. To use this option, you must have selected the Enable Backup with Destination Snapshot in Step 3.11.
Select "Always use when replicating" when you want to replicate always using source snapshots.
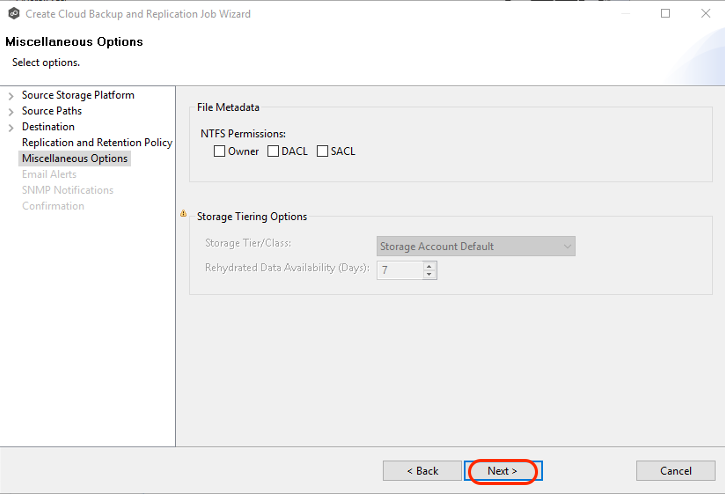
3.15 Select the options to apply to this job. The Miscellaneous options available depend on the destination storage platform selected.NTFS Permissions: If you want NTFS permissions metadata included in the replication, select the elements to include:
Owner – The NTFS Creator-Owner who owns the object (which is, by default, whomever created it).
DACL – A Discretionary Access Control List identifies the users and groups that are assigned or denied access permissions on a file or folder.
SACL - A System Access Control List enables administrators to log attempts to access a secured file or folder. It is used for auditing.
3.16 On the Email Alerts window, click "Select" to select existing email alerts from the drop-down list. Click "Ok", then click "Next".
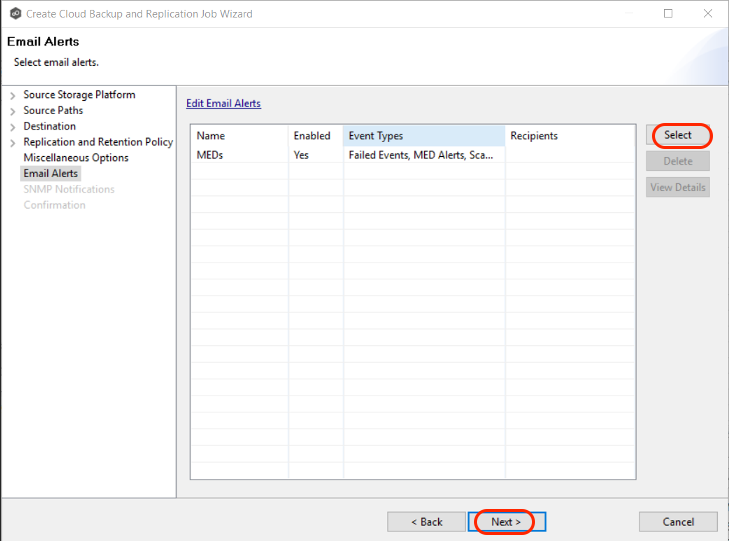
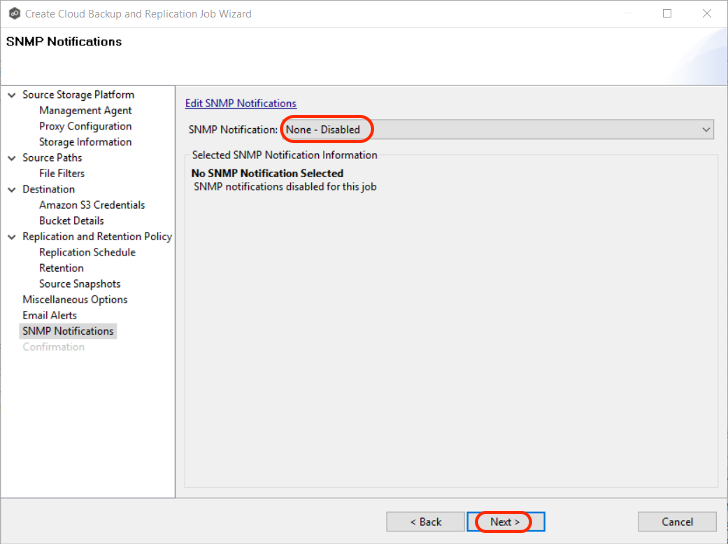
3.17 Select an SNMP notification (optional) from the drop-down list. To disable, select "None - Disabled". Click "Next".
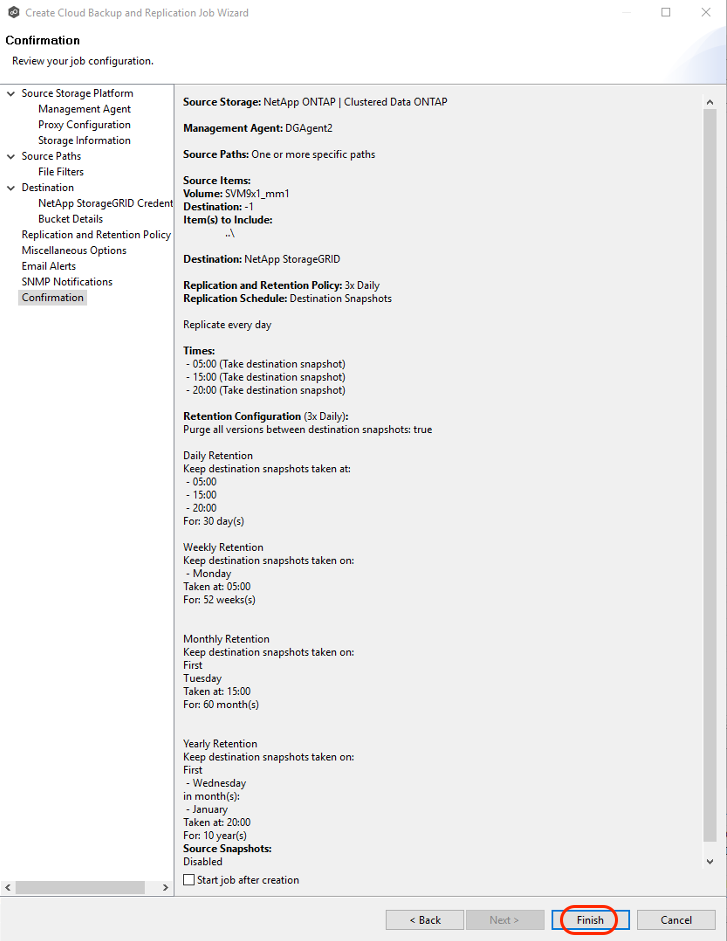
3.18 Review the job configuration on the Confirmation page. Select the "Start job after creation" checkbox if you want the job to start immediately. Click "Finish".
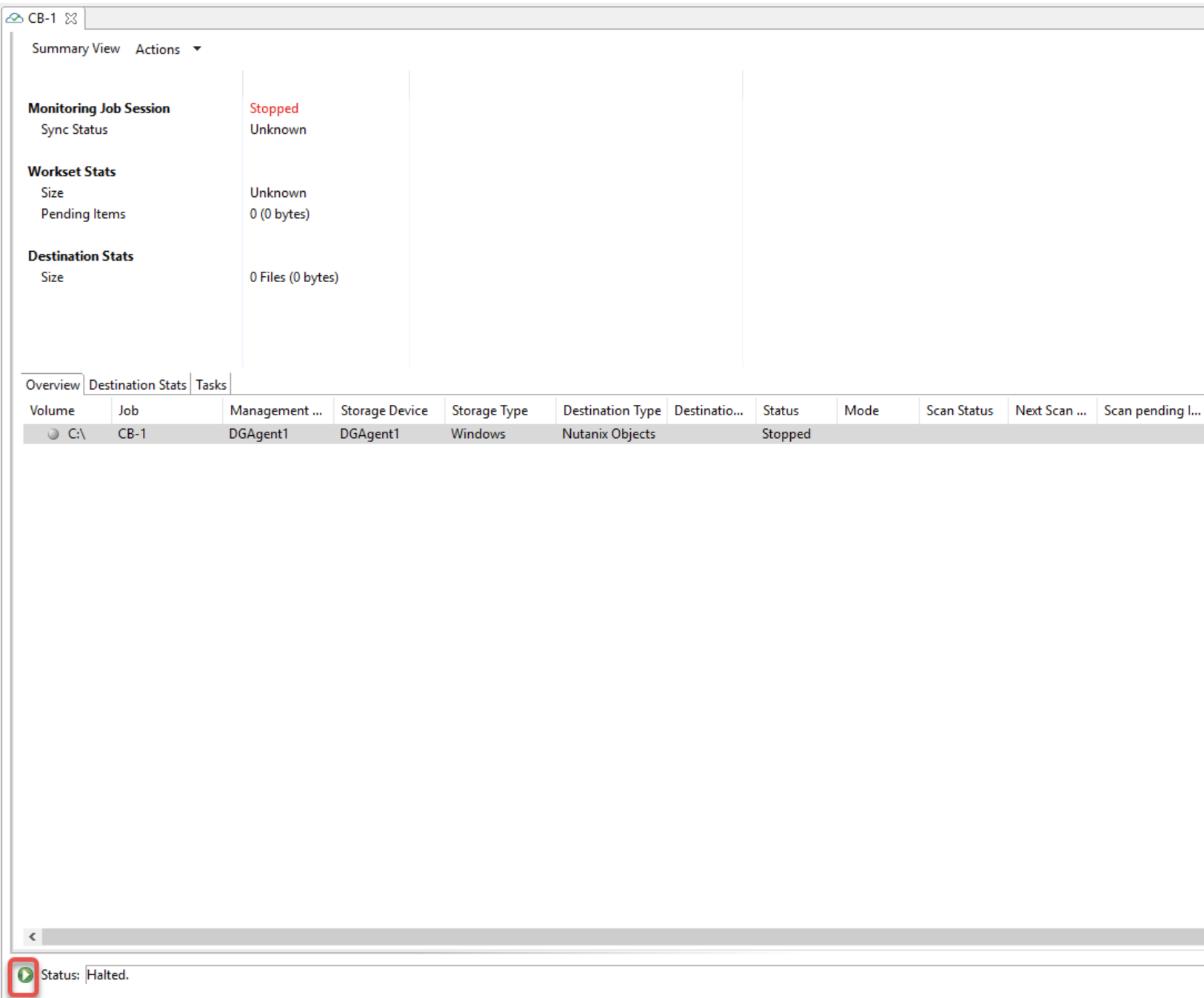
3.19 The Summary tab in the Cloud Backup and Replication Job runtime view is displays the status of the job.
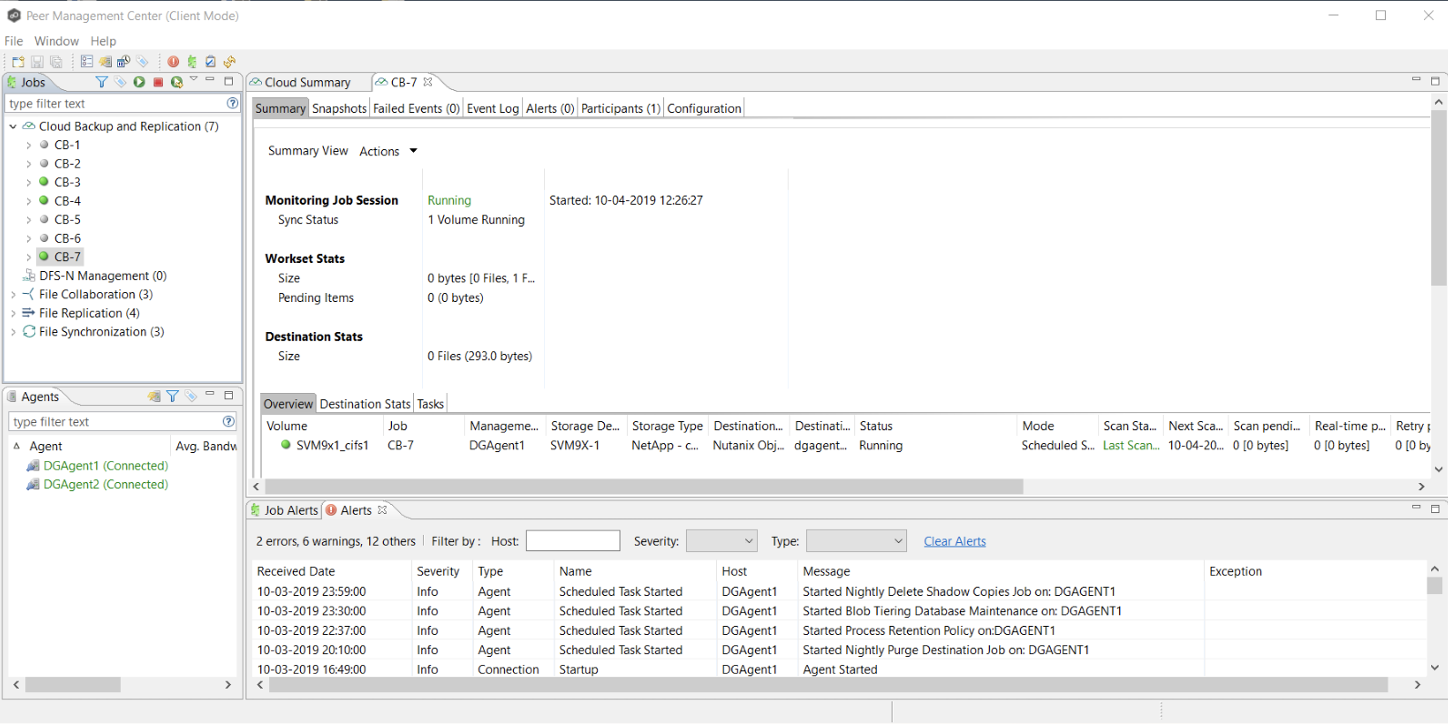
3.20 Jobs can be manually started by righ-clicking the job name in the Jobs view and opening the job. Then click the Start/Stop button next to the status at the bottom-left of the job's view. Then click "Yes" in the confirmation dialog box. When the job starts running, the icon next to the job's name turns green in color.
4. Recovering Data from Backups
For procedure to recover data refer to Recovering Data.
Please contact Peer Software Support for more information or issues at support@peersoftware.com