How does SSE-C Encryption work with Wasabi?
Wasabi supports Server-side encryption with customer-provided encryption keys (SSE-C) that allow you to set your own encryption keys. With the encryption key you provide as part of your request, Wasabi manages the encryption as it writes to disks and decryption when you access your objects. Therefore, you don't need to maintain any code to perform data encryption and decryption. The only thing you do is manage the encryption keys you provide.
Wasabi does not store the encryption key you provide. Instead, it stores a randomly salted HMAC value of the encryption key to validate future requests. The salted HMAC value cannot be used to derive the value of the encryption key or to decrypt the contents of the encrypted object. That means if you lose the encryption key, you lose the object. If you lose the encryption key, any GET request for an object without its encryption key fails, and you lose the object.
This document demonstrates the working of SSE-C on the Wasabi system through a third-party S3 application AWS CLI. Customers can use any supported mechanism to do this based on their requirements.
Demonstrate Server-Side Encryption With Customer-Provided Key
(CLI commands and output screenshots attached)
For this demo, we are performing these four tasks:
Generate a random Key using the OpenSSL command on CLI and name the Key as
wasabi-SSE-C.Key.Upload a file called
wasabi-hello.txtwith SSE-C encryption to a bucket.Download that file with the
wasabi-SSE-C.KeyKey.Download that file without using the
wasabi-SSE-C.KeyKey to see an error.
Instructions:
Generate a random Key using the OpenSSL command on CLI and name the Key as
wasabi-SSE-C.Key.$ openssl rand 32 -out wasabi-SSE-C.Key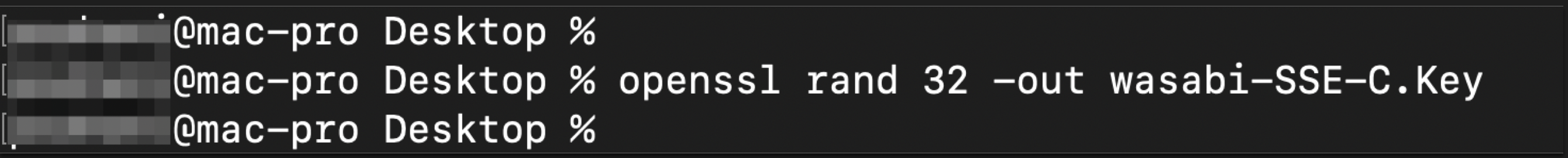
Upload a file called
wasabi-hello.txtwith SSE-C encryption to a bucket.This example discusses the use of Wasabi's us-east-2 storage region. To use other Wasabi storage regions based on your bucket location, use the appropriate Wasabi service URL.
$ aws s3 cp wasabi-hello.txt s3://wasabi-aws-cli-lab-encryption-bucket --sse-c AES256 --sse-c-key fileb://wasabi-SSE-C.Key --profile --endpoint-url=https://s3.us-east-2.wasabisys.com.png)
Download that file with the wasabi-SSE-C.Key Key.
$ aws s3 cp s3://wasabi-aws-cli-lab-encryption-bucket/wasabi-hello.txt local-machine-download.txt --sse-c AES256 --sse-c-key fileb://wasabi-SSE-C.Key --profile --endpoint-url=https://s3.us-east-2.wasabisys.com.png)
Download that file without using the wasabi-SSE-C.Key Key to see an error.
$ aws s3 cp s3://wasabi-aws-cli-lab-encryption-bucket/wasabi-hello.txt local-machine-download.txt --profile --endpoint-url=https://s3.us-east-2.wasabisys.com.png)
For Using SSE-C Encryption With REST API
At the time of object creation with the REST API, you can specify server-side encryption with customer-provided encryption keys (SSE-C). When you use SSE-C, you must provide encryption key information using the following request headers.
Name | Description |
|---|---|
| Use this header to specify the encryption algorithm. The header value must be "AES256.” |
| Use this header to provide the 256-bit, base64-encoded encryption key for Wasabi to use to encrypt or decrypt your data. |
| Use this header to provide the base64-encoded 128-bit MD5 digest of the encryption key according to RFC 1321. Wasabi uses this header for a message integrity check to ensure that the encryption key was transmitted without error. |