Use case:
In some scenarios, you may wish to separate users at the folder level (users share a common bucket but each user has their own folder that is not accessible by other users with access to the same bucket).
At a high level, the following steps are involved:
Create or log into your Wasabi root account
Create a storage bucket for users to share
Create sub-users
Create an IAM policy for each sub-user that limits their access to just their folder within storage bucket
Attach the IAM policy to your sub-user
For this article, let's consider a Wasabi account that manages storage for multiple companies, with multiple clients in a company. Each Company has its own storage bucket, and each client within a company has their own folder they need private access to within that bucket. Let’s take Company-A for example that has two clients, Dollar Bill and Dave Starsky. These two clients cannot see each other’s data, so they will be given access to their own folders within the company bucket.
Bucket Name:
bucket-company-a
Sub-users:
dollar-bill
dave-starsky
Execution Steps:
Let's start by creating folder access separation for sub-user 'dollar-bill'
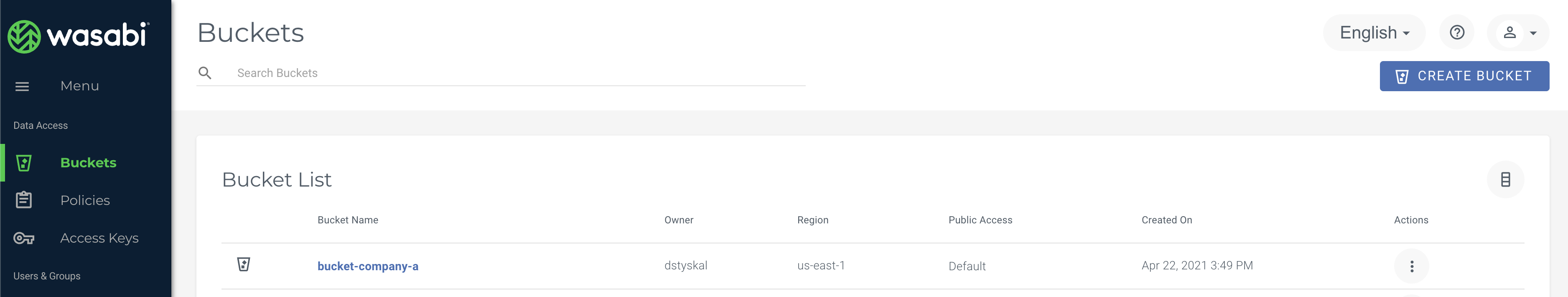
1) Create Bucket
Create a bucket for Company-A, in this case we will call it 'bucket-company-a'
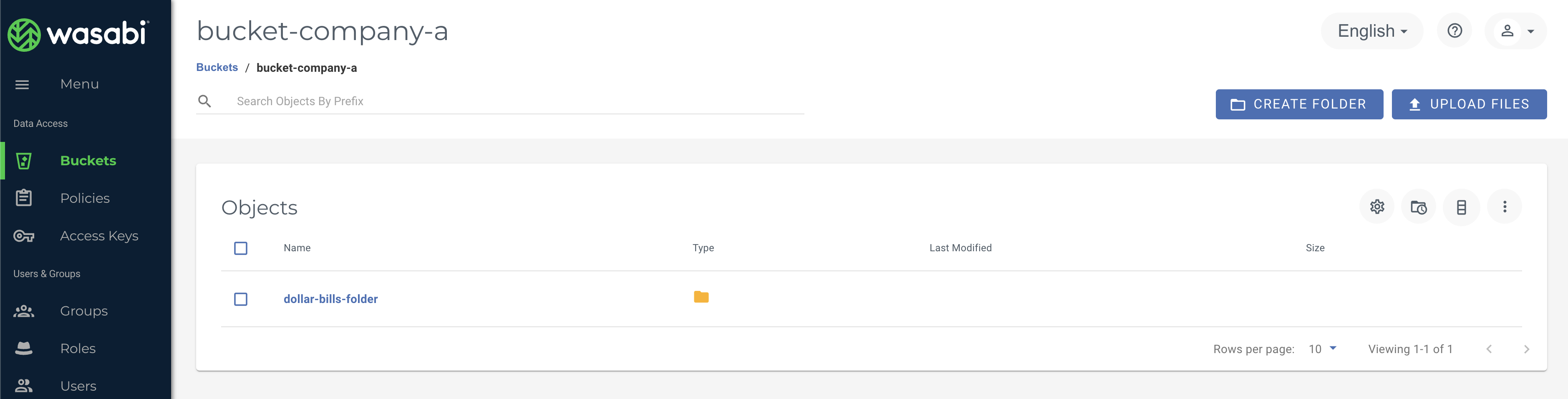
2) Create folder within bucket for sub-user 'dollar-bill'
In this case we will call the folder 'dollar-bills-folder'
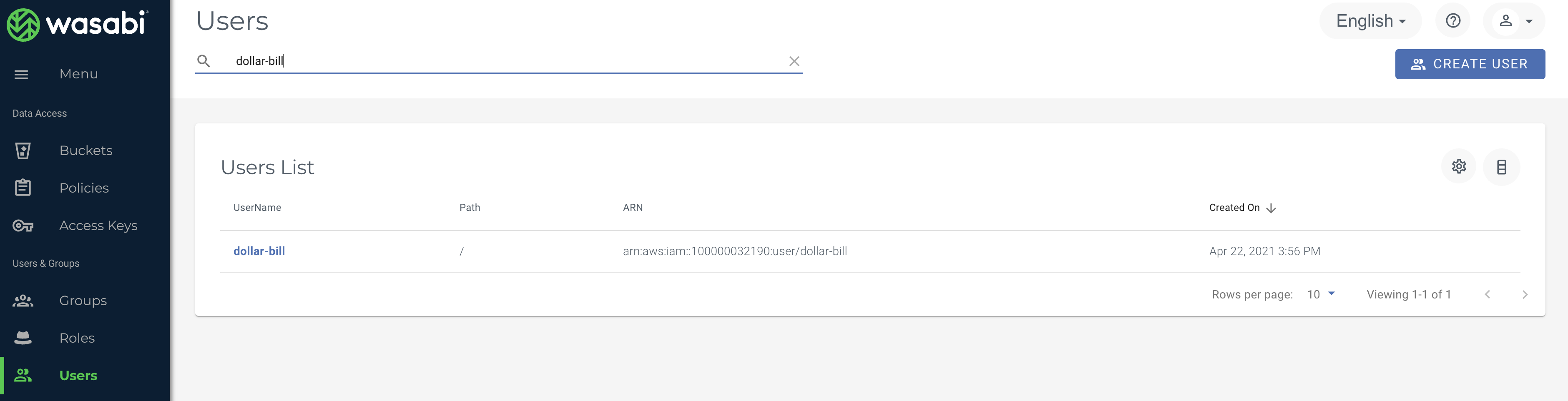
3) Create User
Create sub-user to give folder access to, 'dollar-bill'
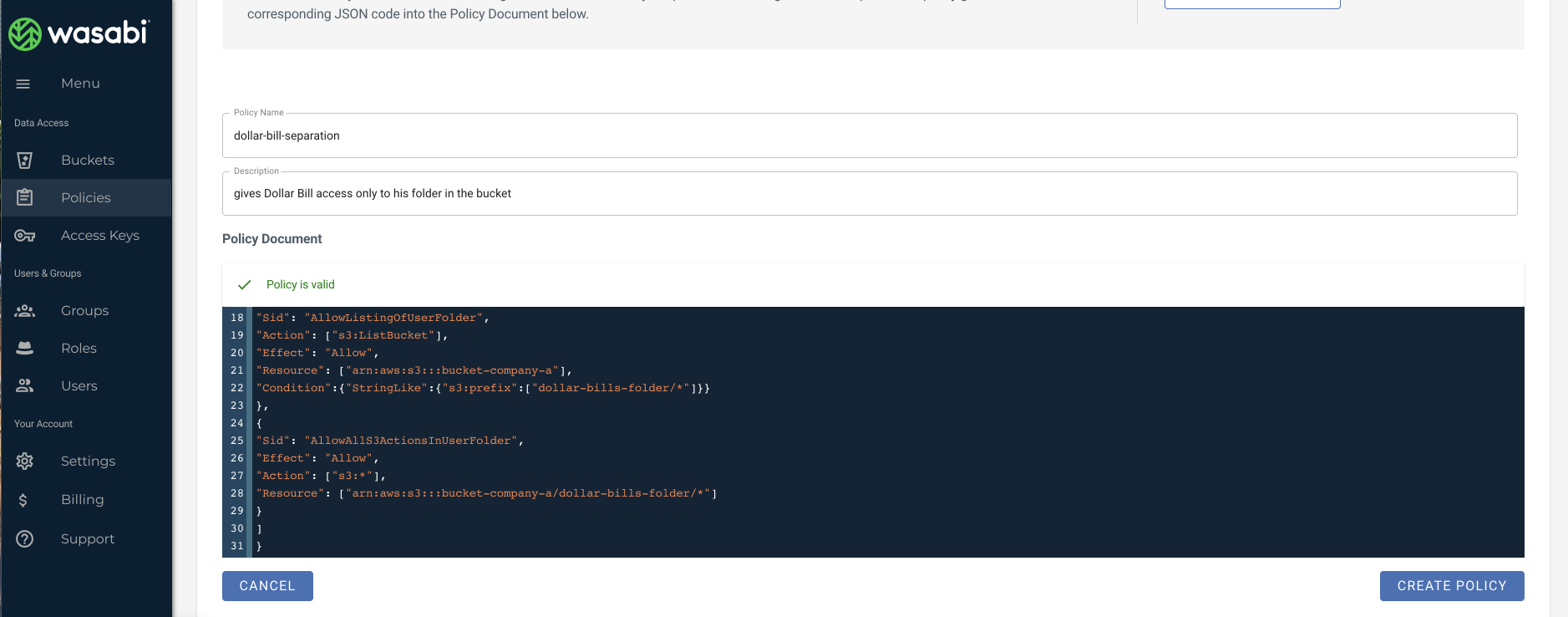
4) Create an IAM policy
From the Wasabi web console UI, choose the Policies -> Create Policy option to create a policy using the example below.
The actual policy syntax for limiting sub-user 'dollar-bill' access to his folder 'dollar-bills-folder' inside the bucket 'bucket-company-a' is provided below (this needs to be edited with your own bucket and folder names in your actual use case).
{
"Version":"2012-10-17",
"Statement": [
{
"Sid": "AllowUserToSeeBucketListInTheConsole",
"Action": ["s3:ListAllMyBuckets", "s3:GetBucketLocation", "s3:GetBucketCompliance"],
"Effect": "Allow",
"Resource": ["arn:aws:s3:::*"]
},
{
"Sid": "AllowRootAndHomeListingOfCompanyBucket",
"Action": ["s3:ListBucket"],
"Effect": "Allow",
"Resource": ["arn:aws:s3:::bucket-company-a"],
"Condition":{"StringEquals":{"s3:prefix":["","dollar-bills-folder/"],"s3:delimiter":["/"]}}
},
{
"Sid": "AllowListingOfUserFolder",
"Action": ["s3:ListBucket"],
"Effect": "Allow",
"Resource": ["arn:aws:s3:::bucket-company-a"],
"Condition":{"StringLike":{"s3:prefix":["dollar-bills-folder/*"]}}
},
{
"Sid": "AllowAllS3ActionsInUserFolder",
"Effect": "Allow",
"Action": ["s3:*"],
"Resource": ["arn:aws:s3:::bucket-company-a/dollar-bills-folder/*"]
}
]
}
5) Attach the above-created policy to sub-user 'dollar-bill'
Navigate to User --> your sub-user (dollar-bill in this case) ---> Policies and attach the above-created policy to them
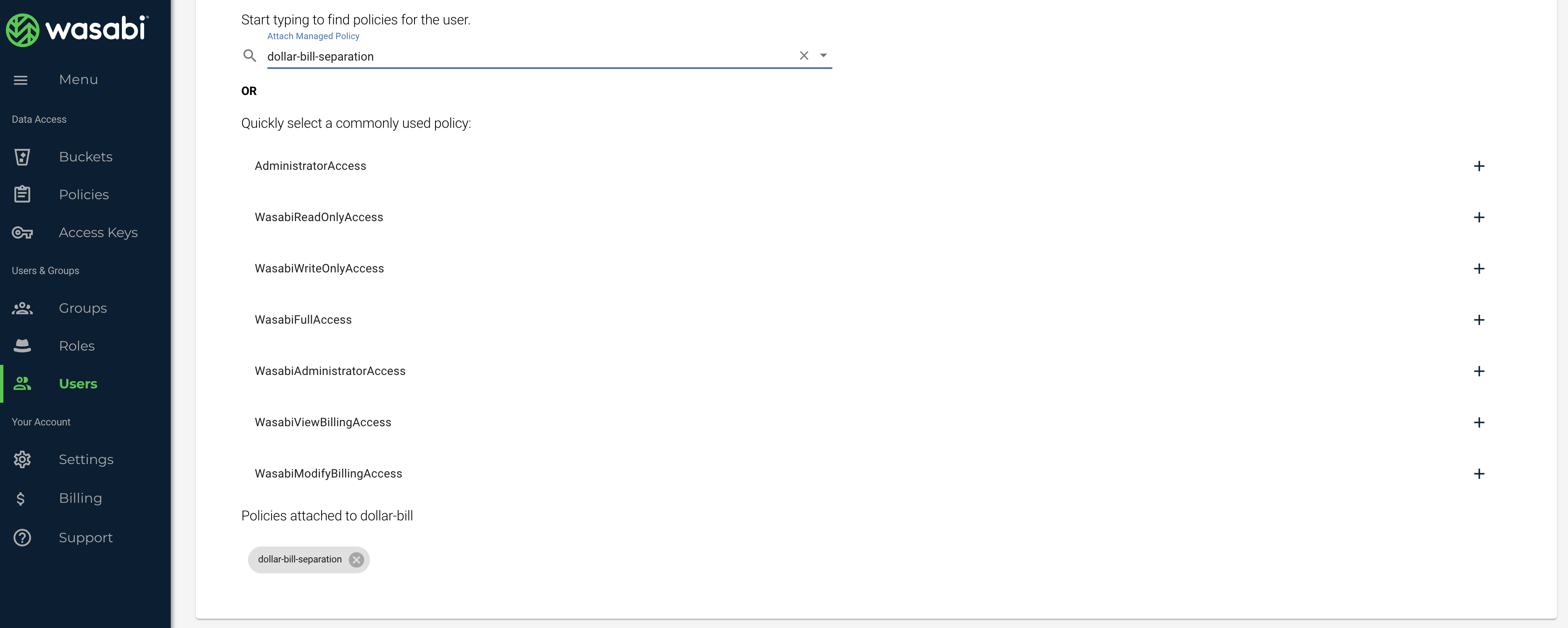
Now this sub-user will be able to access ONLY their folder within that bucket.
------------------------------------------------------------------------------------------------------
Now for sub-user 'dave-starsky'
Repeat the same exact process as above
Create a folder in the Bucket 'bucket-company-a' , for example, a folder called 'dave-starskys-folder'
Create a sub-user 'dave-starsky'
Create an IAM Policy that will give access to the appropriate folder within a bucket for this sub-user, see how the folder name is different in the below policy example
{
"Version":"2012-10-17",
"Statement": [
{
"Sid": "AllowUserToSeeBucketListInTheConsole",
"Action": ["s3:ListAllMyBuckets", "s3:GetBucketLocation", "s3:GetBucketCompliance"],
"Effect": "Allow",
"Resource": ["arn:aws:s3:::*"]
},
{
"Sid": "AllowRootAndHomeListingOfCompanyBucket",
"Action": ["s3:ListBucket"],
"Effect": "Allow",
"Resource": ["arn:aws:s3:::bucket-company-a"],
"Condition":{"StringEquals":{"s3:prefix":["","dave-starskys-folder/"],"s3:delimiter":["/"]}}
},
{
"Sid": "AllowListingOfUserFolder",
"Action": ["s3:ListBucket"],
"Effect": "Allow",
"Resource": ["arn:aws:s3:::bucket-company-a"],
"Condition":{"StringLike":{"s3:prefix":["dave-starskys-folder/*"]}}
},
{
"Sid": "AllowAllS3ActionsInUserFolder",
"Effect": "Allow",
"Action": ["s3:*"],
"Resource": ["arn:aws:s3:::bucket-company-a/dave-starskys-folder/*"]
}
]
}Lastly, attach this policy to the 'dave-starsky' sub-user.
If your company has hundreds and thousands of sub-users requirement, you may use an automated approach to do this as shown here