Use case:
In some scenarios, you may wish to separate users at the bucket level (each sub-user has their own bucket and while a sub-user can access their own bucket, they can't access other sub-users buckets).
At a high level, the following steps are involved:
Create or log into your Wasabi root account
Create a storage bucket for each sub-user
Create sub-user(s)
Create an IAM policy for each sub-user that limits their access to just their storage bucket
Attach the IAM policy to your sub-user
For this article, let's consider a company account with two sub-users
panjack
stonecold
Execution Steps:
Let's walk through this bucket separation for sub-user 'panjack'
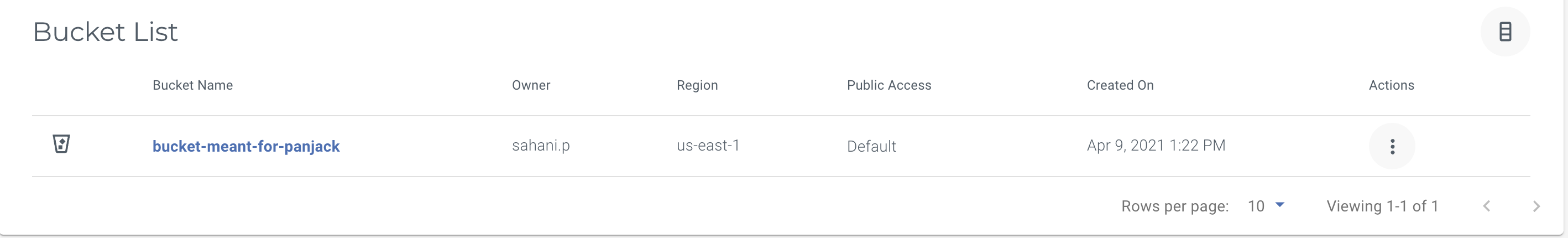
1. Create a bucket
In this example, we are creating a bucket called 'bucket-meant-for-panjack'
2. Create user
In this example, we are creating a sub-user called 'panjack'
.png)
3. Create an IAM policy
From the Wasabi web console UI, choose the Policies -> Create Policy option to create a policy using the example below.
The actual policy syntax for limiting sub-user 'panjack' access to bucket 'bucket-meant-for-panjack' is provided below (this needs to be edited with your own bucket name in your actual use case).
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "arn:aws:s3:::*"
},
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::bucket-meant-for-panjack",
"arn:aws:s3:::bucket-meant-for-panjack/*"
]
}
]
}.png)
Note: To perform any bucket/object operations through the console the sub-user MUST have "ListAllMyBuckets" permission. This will allow the sub-user to list all the buckets when logged into the console but can access content only from the bucket that the sub-user has permission to
4. Attach the above-created policy to sub-user 'panjack'
Navigate to User --> your sub-user (panjack in this case) ---> Policies and attach the above-created policy to them
.png)
Now this sub-user will ONLY be able to access their own bucket
------------------------------------------------------------------------------------------------------
Now for sub-user 'stonecold'
Repeat the same exact process as above
Create Bucket, for example, a bucket called 'bucket-meant-for-stonecold'
Create sub-user 'stonecold'
Create an IAM Policy that will have the appropriate bucket name for this sub-user, see how the bucket name is different in the below policy example
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "arn:aws:s3:::*"
},
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::bucket-meant-for-stonecold",
"arn:aws:s3:::bucket-meant-for-stonecold/*"
]
}
]
}Finally, attach this policy to 'stonecold' sub-user
------------------------------------------------------------------------------------------------------
If your company has hundreds and thousands of sub-users requirement, you may use an automated approach to do this as shown here