How do I use Fortinet's Fortigate NGFW with Wasabi?
FortiGate NGFWs deliver industry-leading enterprise security for any edge at any scale with full visibility and threat protection. FortiGate NGFWs are now partnered with Wasabi to extend the visibility & monitoring. Follow instructions below to integrate NGFWs with Wasabi.
Pre-requisites:
FortiOS v6.4.8 Build 1914 or higher recommended
Current FortiGuard subscription that provides current application signatures
Active Wasabi's Hot Cloud Storage subscription
Reference Architecture:
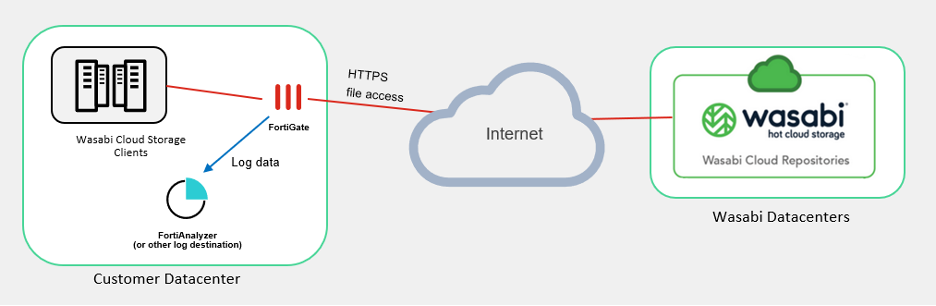
A FortiGate firewall must be in the data path between the Wasabi client and the path to the Wasabi storage regions.
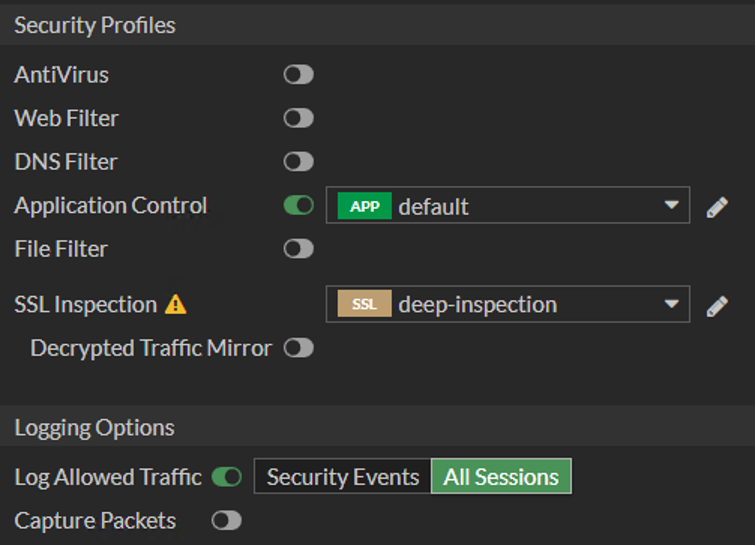
A firewall policy rule should exist with the following:
Permits the desired traffic from the client host to Wasabi
Enables the “Application Control” feature
Enable “deep-inspection” for the SSL Inspection feature
Note: If deep-inspection is disabled, Fortigate firewall will identify traffic being sent-to/received-from Wasabi, when enabled, Fortigate firewall will be able to detect what type of interactions are being exchanged with Wasabi storage (ex: upload vs download vs deletion)
Enable “Log Allowed Traffic” with “All Sessions” option.
To use logging via syslog, go to Log Settings -> Remote Logging and Archiving
Enable the syslog option and enter the destination syslog IP
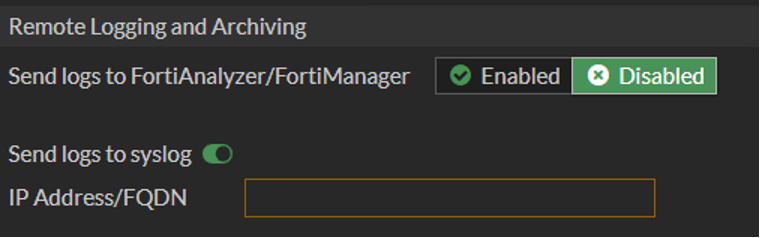
Additionally, FortiAnalyzer can be used as a logging destination, and logs can be accessed via its API or forwarded to a packet capture infrastructure.