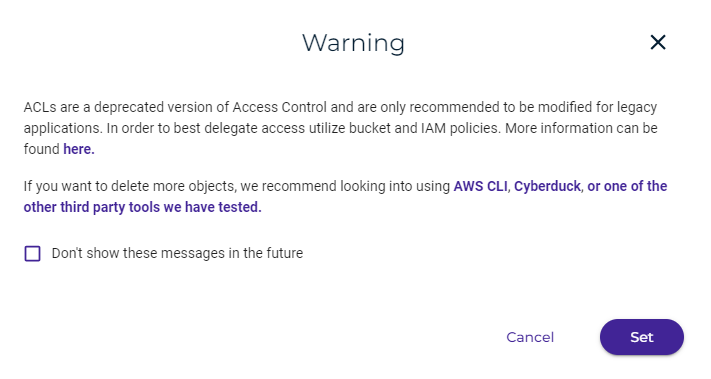
An access control list (ACL) enables you to manage the users and groups that have access to buckets and objects. ACLs are a deprecated version of access control and are only recommended to be modified for legacy applications. Access to buckets is best controlled with bucket policies, as described in Policies. But if you want to use an ACL, follow the instructions below.
Reviewing Access Control
On the Buckets list, click
 for the desired bucket.
for the desired bucket.Click Settings.
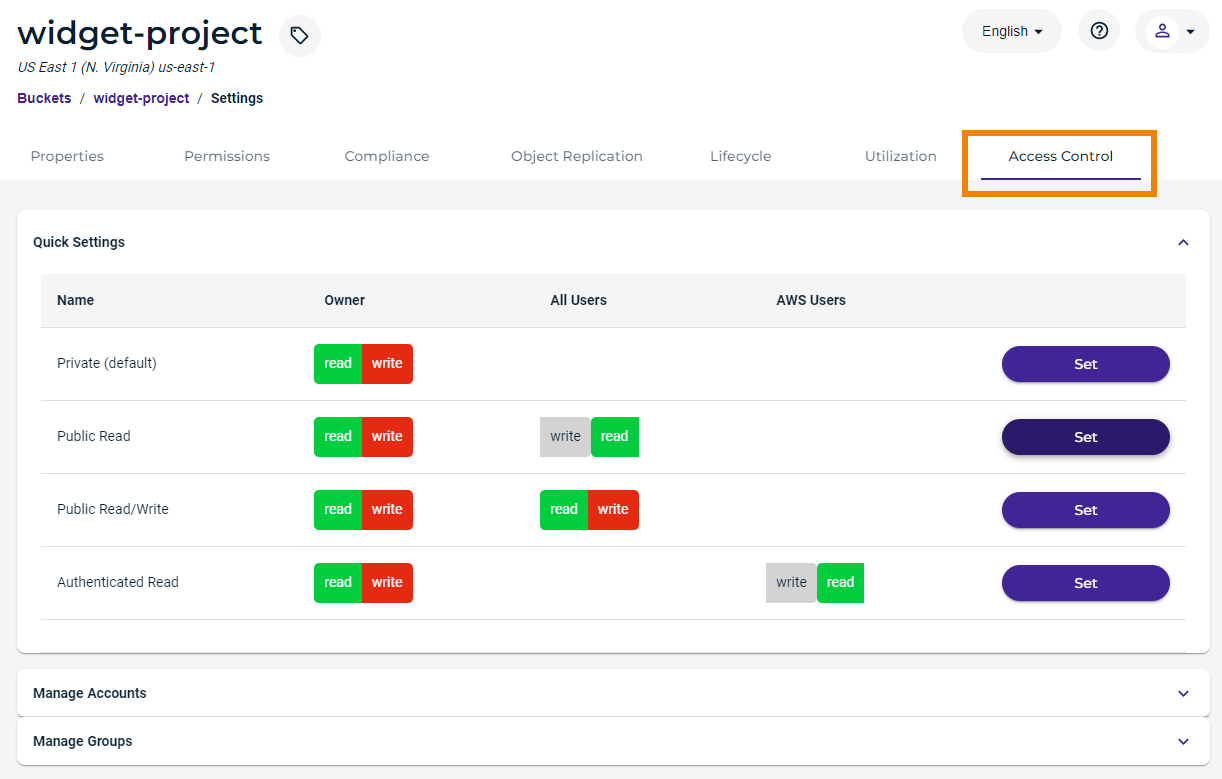
Click the Access Control tab. The Quick Settings panel is displayed. For example:
Setting Access Control
On the Buckets list, click
 for the desired bucket.
for the desired bucket.Click Settings.
Click the Access Control tab. The Quick Settings panel is displayed, as shown above.
Click Set for any access control area you want to change.
Be sure to review the warning message. Then, click Set.