Operations on buckets include: deleting, renaming, and logging buckets as well as cross-origin resource sharing (CORS) support, lifecycle policy, object locking, and compliance.
By default, public use of a bucket, folder, or file is allowed only by certain paid (not trial) accounts. If your account does not have access to this feature, contact Wasabi Support at support@wasabi.com for assistance.
DELETE BUCKET force_delete=true Option
AWS S3 will not allow you to delete a bucket if it contains objects that have not been deleted.
Wasabi provides a force_delete=true option that first deletes all objects in the bucket and then deletes the bucket. The deletion of objects is subject to policy and compliance requirements on the bucket.
To specify the force_delete=true option, add it as a query string. For example:
DELETE http://s3.wasabisys.com/my-bucket?force_delete=true HTTP/1.1Renaming a Bucket
AWS S3 does not support renaming of buckets. It only supports renaming of objects in a bucket.
Wasabi supports the renaming of buckets. The new bucket name must not be in use for the rename to be successful. The caller must have the s3:CreateBucket policy permission to rename a bucket.
To rename a bucket, use the HTTP method MOVE along with the header field “Destination” to give the new bucket name. For example:
MOVE http://s3.wasabisys.com/my_old_bucket HTTP/1.1
Destination: my_new_bucketMFA (Multi-Factor Authentication) Delete
Wasabi supports the “x-amz-mfa” header while:
configuring versioning on a bucket, or
deleting objects with delete object requests compatible with AWS S3.
Wasabi does not require the “x-amz-mfa” header if the user's access credentials signing the request were authenticated with MFA. Wasabi only supports virtual MFA devices.
(Refer also to Workflow for Lifecycle Rule Implementation.)
Checking MFA-Delete Status for an S3 Bucket
To determine whether MFA-Delete is enabled for your S3 bucket, use the get-bucket-versioning command in the AWS CLI:
aws s3api get-bucket-versioning --bucket BUCKETNAME --profile WASABIPROFILE --endpoint-url=https://s3.BUCKETREGION.wasabisys.comThe output will indicate the versioning status and whether MFA-Delete is enabled. For example:
{
"Status": "Enabled",
"MFADelete": "Enabled"
} Status: Enabled indicates that versioning is active.
MFADelete: Enabled confirms that MFA-Delete is enabled for the bucket
Managing MFA-Delete Using the AWS CLI
The following are prerequisites for managing MFA-Delete using the AWS CLI:
Versioning is enabled on the bucket.
Root account credentials are configured with MFA.
AWS CLI v2 is installed.
Use this command to enable MFA-Delete:
aws s3api put-bucket-versioning --bucket BUCKETNAME --versioning-configuration MFADelete=Enabled,Status=Enabled --mfa "arn:aws:iam::ACCOUNTID:mfa/root-account-mfa-device MFACODE” --endpoint-url=https://s3.BUCKETREGION.wasabisys.com –profile WASABIPROFILEUse this command to disable MFA-Delete:
aws s3api put-bucket-versioning --bucket BUCKETNAME --versioning-configuration MFADelete=Disabled,Status=Enabled --mfa "arn:aws:iam::ACCOUNTID:mfa/root-account-mfa-device MFACODE” --endpoint-url=https://s3.BUCKETREGION.wasabisys.com –profile WASABIPROFILEMaximum Number of Buckets
Standard AWS S3 supports only 100 buckets.
Wasabi allows for a maximum of 1000 buckets per account, and this number may be increased by contacting Wasabi Customer Support.
Bucket Logging
Wasabi supports bucket logging, which creates a text log file of all access to a bucket. The format of the log file is identical to the AWS S3 log file.
Wasabi bucket logging does not require any ACL permission settings to store logs in a target bucket. Although you can give permission settings in the logging request or in an ACL, they are not required for logging to work in Wasabi. However, the bucket that is a target for log files must be inside the same account as the bucket being logged.
Bucket Cross-Origin Resource Sharing (CORS) Support
For compatibility with browser access to Wasabi as a web server, the Wasabi server will return CORS headers when the header “Origin” is given in an HTTP request. Additionally, the server supports the HTTP method OPTIONS on either buckets or objects to return the CORS headers needed for a browser pre-flight test before accessing Wasabi.
Different from AWS, Wasabi returns the settings that will allow the browser full access to Wasabi. Hence, Wasabi does not support the AWS functions that allow a PUT and GET on a bucket with the “cors” parameter in the URL. Note that allowing the browser full access to data does not affect the security of access to any objects, and all access policies will still be enforced.
The following are the HTTP headers returned by default when the header “Origin” is given in an HTTP request:
Access-Control-Allow-Headers: *
Access-Control-Allow-Methods: GET, HEAD, POST, PUT, DELETE, MOVE, OPTIONS
Access-Control-Allow-Origin: *
Access-Control-Expose-Headers: *
Access-Control-Max-Age: 86400Event Notifications (SNS)
Wasabi supports the AWS Simple Notification Service (SNS), which is used to configure Event Notifications so you can receive information about specific storage activities that take place on your account.
To use the Event Notifications feature, you must add AWS credentials to the Event Notifications tab on the Console Settings page. Then, configure Event Notifications for each bucket in Bucket Settings.
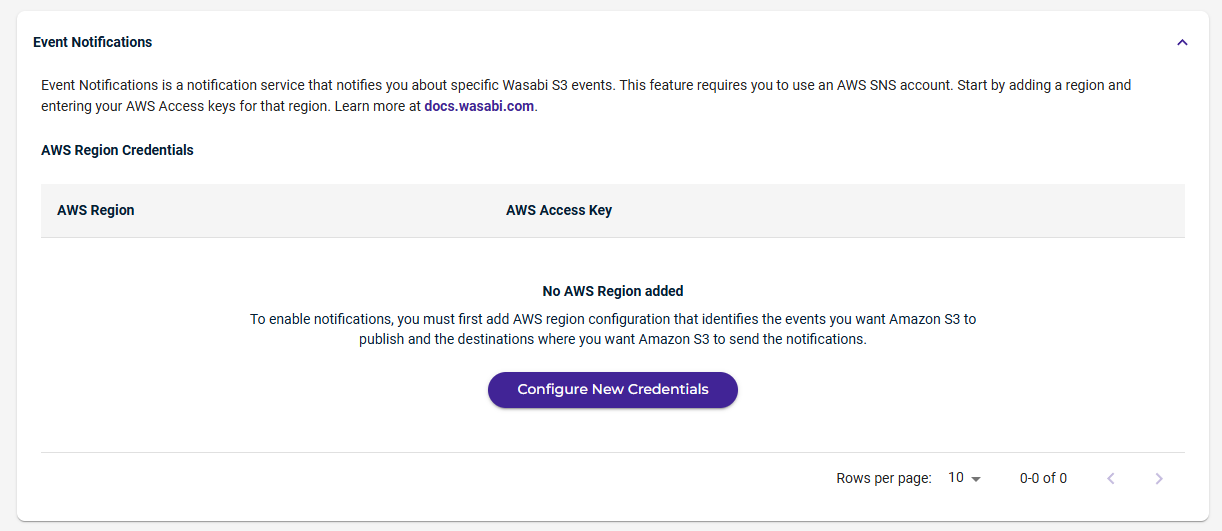
You can define the types of events for which to receive notifications related to specific topics. Subscribers of a topic will then receive those notifications from Wasabi. 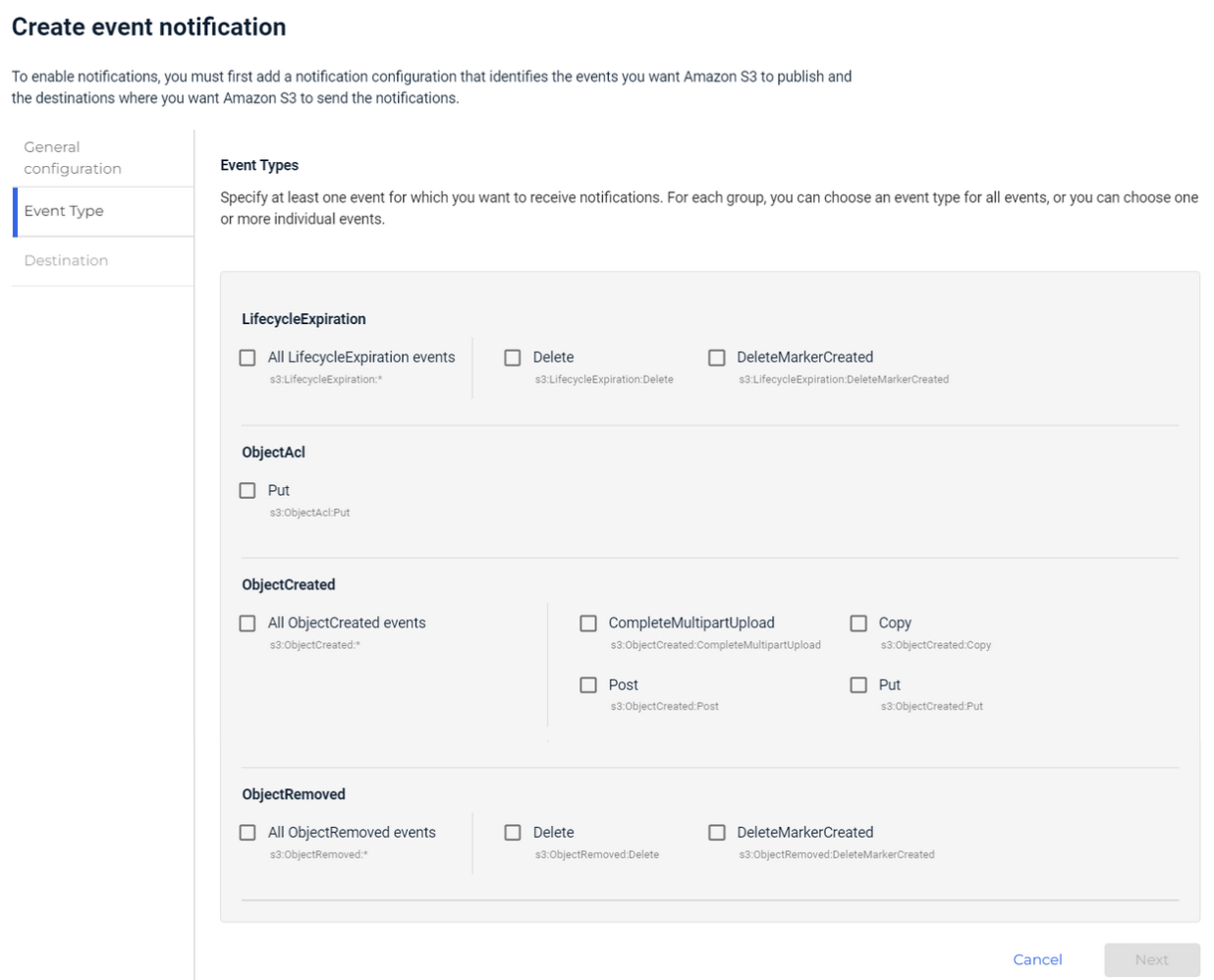
Lifecycle Policy
The Lifecyle feature establishes a Lifecycle policy with rules to define actions that you want Wasabi to take during the life of an object. This feature replaces the need to manually delete an object after a retention period.
Configuring Lifecycle Settings
The lifecycle settings for a bucket are configured with the "put-bucket-lifecycle-configuration" command. For example:
$ aws s3api put-bucket-lifecycle-configuration --bucket 1-1-1-1 --endpoint-url https://s3.wasabisys.com --lifecycle-configuration file://lifecycle.json{
"Rules": [
{
"Expiration": {
"Days": 1
},
"ID": "lifecycle_rule_1",
"Filter": {
"And": {
"ObjectSizeGreaterThan": 1,
"ObjectSizeLessThan": 21474836480
}
},
"Status": "Enabled"
},
{
"Expiration": {
"Days": 1
},
"ID": "object_lifecycle_rule_bucket_6807766",
"Filter": {
"Prefix": "1"
},
"Status": "Enabled"
}
]}Here is another example:
PUT https://s3.wasabisys.com/1-1-1-1?lifecycle
<LifecycleConfiguration xmlns="http://s3.amazonaws.com/doc/2006-03-01/">
<Rule>
<Expiration>
<Days>1</Days>
</Expiration>
<ID>lifecycle_rule_1</ID>
<Filter>
<And>
<ObjectSizeGreaterThan>1</ObjectSizeGreaterThan>
<ObjectSizeLessThan>21474836480</ObjectSizeLessThan>
</And>
</Filter>
<Status>Enabled</Status>
</Rule>
<Rule>
<Expiration>
<Days>1</Days>
</Expiration>
<ID>object_lifecycle_rule_bucket_6807766</ID>
<Filter>
<Prefix>1</Prefix>
</Filter>
<Status>Enabled</Status>
</Rule>
</LifecycleConfiguration>There is no response body for this call.
Retrieving Lifecycle Settings
The lifecycle settings for a bucket can be retrieved with the "get-bucket-lifecycle-configuration" command. For example:
$ aws s3api get-bucket-lifecycle-configuration --bucket 1-1-1-1 --endpoint-url https://s3.wasabisys.com{
"Rules": [
{
"Expiration": {
"Days": 1
},
"ID": "lifecycle_rule_1",
"Filter": {
"And": {
"ObjectSizeGreaterThan": 1,
"ObjectSizeLessThan": 21474836480
}
},
"Status": "Enabled"
},
{
"Expiration": {
"Days": 1
},
"ID": "object_lifecycle_rule_bucket_6807766",
"Filter": {
"Prefix": "1"
},
"Status": "Enabled"
}
]}Here is another example:
GET https://s3.wasabisys.com/1-1-1-1?lifecycle
<?xml version="1.0" encoding="UTF-8"?>
<LifecycleConfiguration xmlns="http://s3.amazonaws.com/doc/2006-03-01/">
<Rule>
<Expiration>
<Days>1</Days>
</Expiration>
<ID>lifecycle_rule_1</ID>
<Filter>
<And>
<ObjectSizeGreaterThan>1</ObjectSizeGreaterThan>
<ObjectSizeLessThan>21474836480</ObjectSizeLessThan>
</And>
</Filter>
<Status>Enabled</Status>
</Rule>
<Rule>
<Expiration>
<Days>1</Days>
</Expiration>
<ID>object_lifecycle_rule_bucket_6807766</ID>
<Filter>
<Prefix>1</Prefix>
</Filter>
<Status>Enabled</Status>
</Rule>
</LifecycleConfiguration>Deleting Lifecycle Settings
The lifecycle settings for a bucket can be deleted with the "delete-bucket-lifecycle" command. For example:
$ aws s3api delete-bucket-lifecycle --bucket 1-1-1-1 --endpoint-url https://s3.wasabisys.comHere is another example:
DELETE http://wasabisys.com/1-1-1-1?lifecycleThere is no response body for this call.
Object Lock
Wasabi supports an object lock that prevents the deletion or overwrite of object versions for a fixed amount of time or indefinitely.
Tag | Description |
|---|---|
ObjectLockConfiguration | This is the mandatory root-level tag for object lock configuration. |
ObjectLockEnabled | This tag must be configured as Enabled. |
Rule | This specifies the object lock rule for a bucket. It requires both a mode and a period. The period can be either Days or Years, but you must select one. You cannot specify Days and Years at the same time. |
The object lock settings for a bucket are specified using the “?object-lock” query string along with the object lock settings as the XML body in the request. For example:
PUT https://s3.wasabisys.com/qa.objectlock.002/?object-lock HTTP/1.1
<ObjectLockConfiguration>
<ObjectLockEnabled>Enabled</ObjectLockEnabled>
<Rule>
<DefaultRetention>
<Mode>COMPLIANCE</Mode>
<Days>10</Days>
</DefaultRetention>
</Rule>
</ObjectLockConfiguration>The object lock settings for a bucket can be retrieved by getting the bucket with the “?object-lock” query string. For example:
GET https://s3.wasabisys.com/qa.objectlock.002/?object-lock HTTP/1.1Response body:
<?xml version="1.0" encoding="UTF-8"?>
<ObjectLockConfiguration xmlns="http://s3.amazonaws.com/doc/2006-03-01/">
<ObjectLockEnabled>Enabled</ObjectLockEnabled>
<Rule>
<DefaultRetention>
<Mode>COMPLIANCE</Mode>
<Days>10</Days>
</DefaultRetention>
</Rule>
</ObjectLockConfiguration>There are also object lock settings for each object described in Operations on Objects.
The object lock settings for a bucket can be cleared using "?object-lock" query string. For example:
PUT https://s3.wasabisys.com/qa.objectlock.002/?object-lock HTTP/1.1Response body:
<ObjectLockConfiguration>
<ObjectLockEnabled>Enabled</ObjectLockEnabled>
<Rule>
<DefaultRetention>
<Mode></Mode>
<Days></Days>
</DefaultRetention>
</Rule>
</ObjectLockConfiguration>Wasabi Compliance
Wasabi supports a compliance policy that prevents the deletion of objects and provides additional information to prove that the original data has not been modified since the time written. The compliance feature may be required for certain regulatory needs, but is also useful to prevent accidental data deletion.
Compliance is different from the object locking setting for a bucket.
You can set the compliance policy on any bucket, controlling all the objects that are stored in that bucket. Specify the bucket compliance policy with the following XML tags.
Tag | Description |
|---|---|
Status | Either “enabled” or “disabled” to turn compliance on and off, respectively. Enabling will immediately apply to all objects in the bucket. |
LockTime | The time at which the compliance settings are “locked”—the settings cannot be reduced by any API call. Once the settings are locked, they cannot be unlocked without the intervention of Wasabi Customer Support. The lock time allows you to support two use cases:
The lock time parameter may be:
|
RetentionDays | An integer for the minimum number of days that objects are always retained after their creation date or release from conditional hold. You can extend the retention date for any individual object, but you may not shorten the date. This parameter is always required. |
ConditionalHold | A Boolean value (“true” or “false”) indicating if newly created objects are placed on conditional hold, meaning that they cannot be deleted until the conditional hold is explicitly turned off. The default is false if this parameter is not given. Note that this setting may be changed even after the settings are locked. |
The compliance settings for a bucket are specified using the “?compliance” query string along with the compliance settings as the XML body in the request. For example:
PUT http://s3.wasabisys.com/my-bucket?complianceHTTP./1.1
<BucketComplianceConfiguration>
<Status>enabled</Status>
<LockTime>off</LockTime>
<RetentionDays>365</RetentionDays>
<DeleteAfterRetention>true</DeleteAfterRetention>
</BucketComplianceConfiguration>After compliance is enabled for a bucket, the policy is immediately applied to all objects in the bucket. An attempt to delete an object before the retention period will return an error.
The compliance settings for a bucket can be retrieved by getting the bucket with the “?compliance” query string. For example:
GET http://s3.wasabisys.com/my-buck?complianceHTTP/1.1Response body:
<BucketComplianceConfiguration xml ns="http://s3.amazonaws.com/doc/2006-03-01/">
<Status>enabled</Status>
<LockTime>2016-11-07T15:08:05Z</LockTime>
<IsLocked>false</IsLocked>
<RetentionDays>0</RetentionDays>
<ConditionalHold>false</ConditionalHold>
<DeleteAfterRetention>false</DeleteAfterRetention>
</BucketComplianceConfiguration>There are also compliance settings for each object described in Operations on Objects.
Operations on Buckets Not Supported in Wasabi
Operation | Description | Individual Operations |
|---|---|---|
Bucket Accelerate | Wasabi does not have an implementation of the AWS S3 bucket accelerate or similar subresource. | GetBucketAccelerateConfiguration, PutBucketAccelerateConfiguration |
Bucket Analytics | Wasabi does not support bucket analytics configurations. | DeleteBucketAnalyticsConfiguration, GetBucketAnalyticsConfiguration, ListBucketAnalyticsConfigurations, PutBucketAnalyticsConfiguration |
Bucket Encryption | As Wasabi does not support AWS Key Management Service (KMS) keys for encryption, bucket encryption API calls are not supported. | DeleteBucketEncryption, GetBucketEncryption, PutBucketEncryption |
Bucket Intelligent Tiering | Wasabi does not support intelligent tiering configurations. | DeleteBucketIntelligentTieringConfiguration, GetBucketIntelligentTieringConfiguration, ListBucketIntelligentTieringConfigurations, PutBucketIntelligentTieringConfiguration |
Bucket Metadata Table | Wasabi does not support bucket metadata table configurations. | CreateBucketMetadataTableConfiguration, DeleteBucketMetadataTableConfiguration, GetBucketMetadataTableConfiguration |
Bucket Metrics | Wasabi does not support the operations to receive one-minute CloudWatch metrics, set CloudWatch alarms, and access CloudWatch dashboards to view near-real-time operations and performance. | DeleteBucketMetricsConfiguration, GetBucketMetricsConfiguration, ListBucketMetricsConfigurations, PutBucketMetricsConfiguration |
Bucket Ownership Controls | Wasabi does not support bucket ownership controls. | DeleteBucketOwnershipControls, GetBucketOwnershipControls, PutBucketOwnershipControls |
Bucket Request Payment | Wasabi does not support the use of the “requestPayment” subresource for buckets. | PutBucketRequestPayment |
Bucket Website | Website configuration is unavailable in Wasabi. Given the nature of Wasabi as a long-term object store, we do not expect to support website operations on buckets. The header “x-amz-website-redirect-location” is ignored in any object requests. | DeleteBucketWebsite, PutBucketWebsite |
S3 Block Public Access | Wasabi does not support the operation to centrally block existing public access (whether made possible via an ACL or a policy) and make sure newly created items are not inadvertently granted public access. | DeletePublicAccessBlock, GetPublicAccessBlock, PutPublicAccessBlock, GetBucketPolicyStatus |
Object Operations | Wasabi does not support some operations related to individual objects. | GetObjectAttributes, GetObjectTorrent, RestoreObject, WriteGetObjectResponse |
S3 Select | Wasabi does not support the S3 Select API. | SelectObjectContent |
S3 Session | Wasabi currently does not support directory buckets, which means there is no support for CreateSession API as a result. Wasabi supports getting temporary credentials through STS operations. | CreateSession |
Bucket policies do not support use of the “s3:x-amz-server-side-encryption-customer-algorithm” header under the null context key in the condition element. However, this header is supported on an object-level via the S3 API. For more information about supported IAM and STS operations and policy variables, refer to IAM and STS Support With the Wasabi S3 API.